I have done a series of blog post on preparing your KMS environment for Windows 10 activation. You should be set to go but the final step you need to take is update the KMS Service Host Key. That means that in a corporate environment you’ll need to get your KMS Service updated so you can active the Windows 10 clients.
This one has tripped up some people when it comes to finding it. So we’ll address that here is as well.
Please note that only Windows Server 2012 (R2) or Windows 8, 8.1 or 10 can act as KMS Service Hosts.
Preparations
On the Volume License Servicing Center you cannot only get the bits but also the MAK and KMS keys. Normally you’d go directly to Downloads and Keys, filter down to what you’re looking for and find your KMS host key over there.That works for the Windows clients as before. But you cannot find and updated KMS Service key right now for Windows Server, that will probably work again when Windows Server 2016 goes RTM.
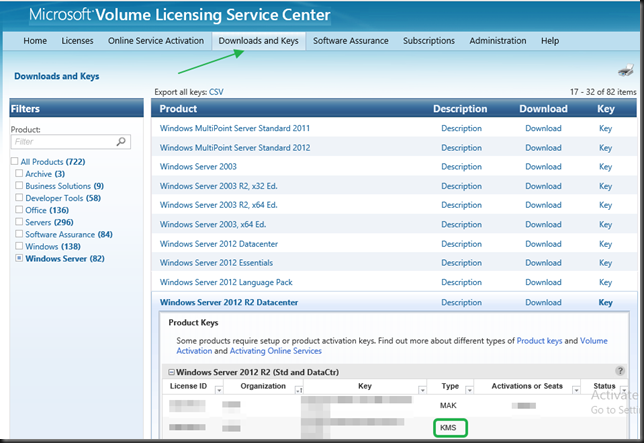
But for now you need to get the key by using a bit of a different path than you’re used to. Got to Licenses and select Relationship Summary
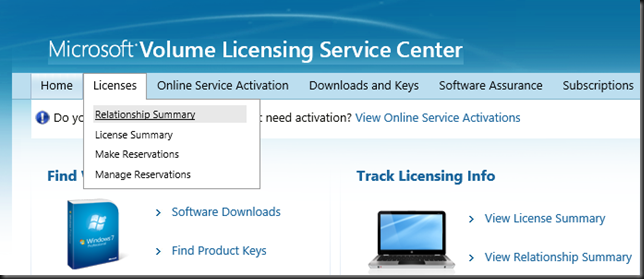
Navigate to the correct license id and click it to open the details of your license. There you select Product Keys
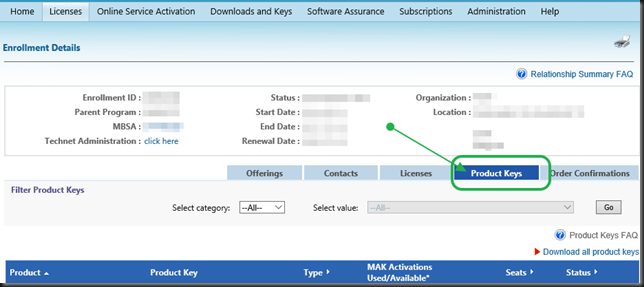
In the list of keys under that license you’ll find the KMS keey you need under product key for the product Windows Srv 2012R2 DataCtr/Std KMS for Windows 10

The Windows 10 KMS client keys are listed publicly by Microsoft. They are the keys of clients that activate against a KMS server. If you have you volume licensing media that’s normally the one in box with the client. You can read more in my blog Windows 10 KMS Client Setup Keys. If you don’t want or cannot use a KM you’ll need to use MAK keys on the clients. These are found on the Volume License Servicing Center as well when you have a valid license.
You also need to have installed an update on your KMS Service hosts. You can read all about that in my blog post KB3058168: Update that enables Windows 8.1 and Windows 8 KMS hosts to activate Windows 10 If you don’t install this update registering a Windows 10 KMS key will throw an error:
0xc004f015: The Software Licensing Service reported that the license is not installed.
SL_E_PRODUCT_SKU_NOT_INSTALLED
So grab the hotfix if it isn’t installed via Windows Update, WSUS etc. and install it from an elevated command prompt. Just follow the instructions and you’ll be fine 
Upgrading the KMS Service Host Key
It goes without saying that we’ll need to update the KMS Service Host key or we’ll see error 0xC004F015:
0xc004f042 – SL_E_VL_KEY_MANAGEMENT_SERVICE_ID_MISMATCH
he Software Licensing Service determined that the specified Key Management Service (KMS) cannot be used.
This is also described in KB 3086418 Error 0xC004F015 while activating Windows 10 Enterprise using Windows Server 2012 R2 KMS Host
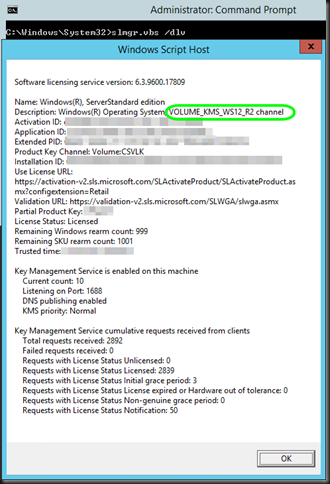
We take a look at our current situation by running slmgr.vbs /dlv which show us a Wk212R2 KMS Service host which can activate all servers & clients up to Windows 8.1/ Windows Server 2012 R2.
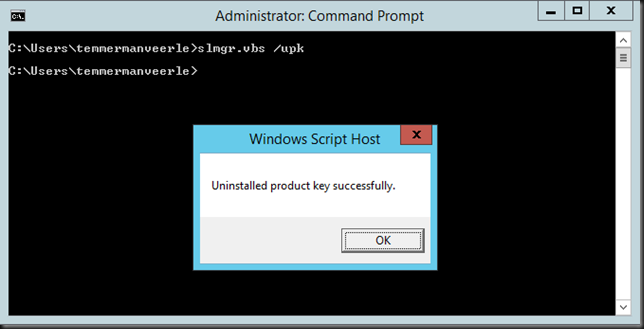
Uninstall the current please use an elevated command prompt 
Now you can install the new Windows Srv 2012R2 DataCtr/Std KMS for Windows 10 key. If you run in to any issues here, restarting the KMS Service can help ((“net stop sppsvc” and “net start sppsvc“) . Try that first.
slmgr.vbs /ipk PIRAT-ESARE-NOTGE-TTING-AKEY!
Be patient, it’s not instantaneous.
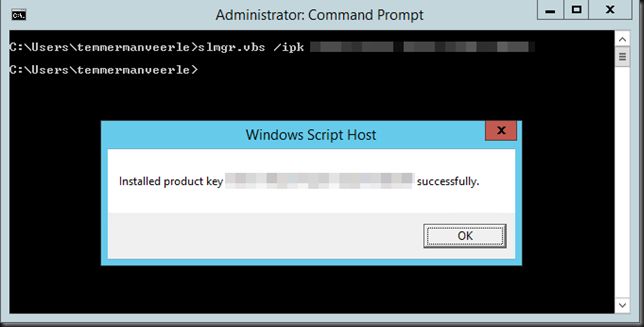
Fall you wannabe pirates out there, that’s not a real key. As far as you are concerned this is the Navy  . If you’re, looking for illegal keys, cracks, keygens, activators or dodgy KMS virtual machines and such this is not the place!
. If you’re, looking for illegal keys, cracks, keygens, activators or dodgy KMS virtual machines and such this is not the place!
Show what’s up and running now by running slmgr.vbs /dlv again and as you can see we’re in business to activate all our Windows Server 2012 R2 and Windows 10 machines as well as all lower versions down to Windows Server 2008 an Windows Vista.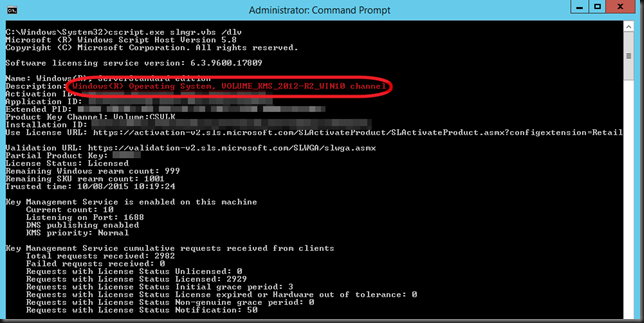
So we’re ready to roll out Windows 10 now via MDT and have our KMS server activate them.
![]()