Presenting at Experts Live 2019 Europe in Prague
I am happy to announce that I will be presenting at Experts Live 2019 Europe in Prague. The conference is held between 20-22 November 2019. This is my first time speaking there and I am really looking forward to it.

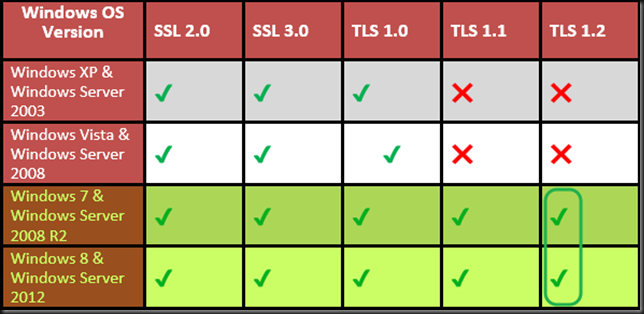
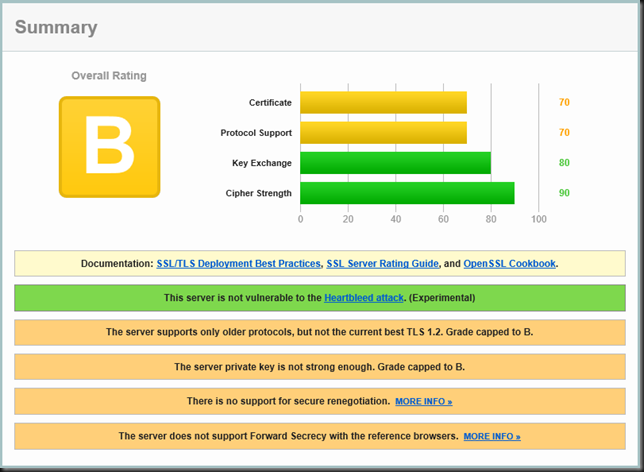
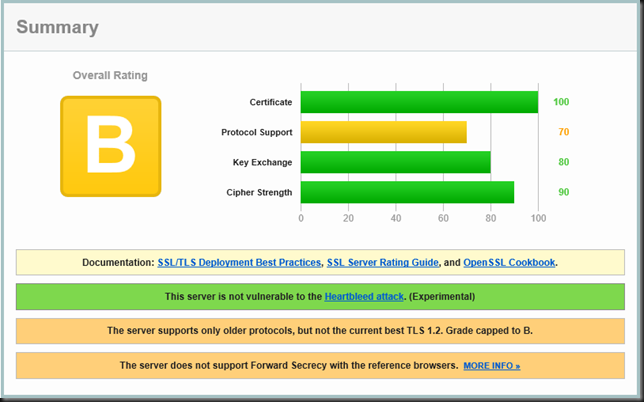
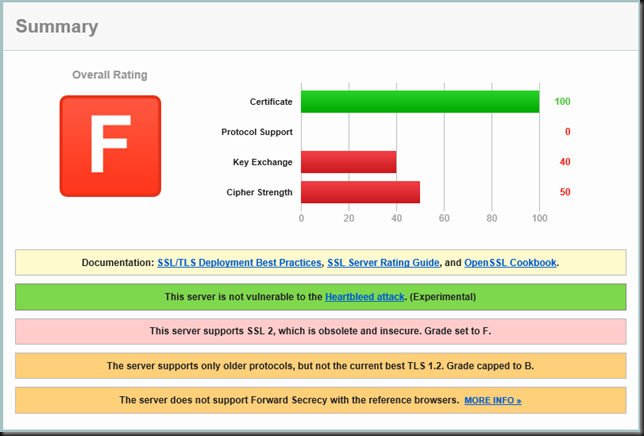
I will be talking about Hyper-V backups, the good, the bad and the ugly. Many people are still on older Windows Server versions and the improvements in backup alone should make for a strong use case to upgrade. I’ll show you why. I’ll share details improvements in speed, reliability, and scalability no matter what storage technology you use. Local, HCI, SAN, … they all benefit. We’ll share tips on how to leverage the improvements for the best results and make you backups shine. Finally, we’ll provide some feedback on what is still needs improvement. Remember as long as you run workloads on virtual machines you have to maintain it, keep it up to date and protected! If you know all this already, no worries, come for the over 40 other experts presenting. Take a look at the session catalog and see for your self.
Join us!
The conference focusses on Microsoft technologies at large and deals with Cloud, Datacenter, Security, Identity Management and the Modern Workplace. As such it realizes there is a lot of variety out there in building blocks used to make a company run. This means it offers content that reflects that reality and helps people succeed in their digital efforts to help their businesses run smoothly and securely on-premises as well as in the hybrid and public cloud.
I encourage you to attend if you have the opportunity. The content of other Experts Live Conferences I have done in the past was always excellent and the speakers were very knowledgeable. The same goes for Experts Live Europe I hear from my fellow MVP and colleagues who have attended before. Note that It is right after Microsoft Ignite 2019 and there are quite a lot of Microsoft attending as well. This means you’ll be getting some new information and insights hot of the press.
Life long learning is fun and doesn’t only happen at your desk or in a course. Get out of the office and into the world. It helps to get rid of the blinders and widen your view and vision on what is possible. It helps to learn from others, from your peers. So don’t delay and register here
Network, socialize, share and learn
With so many colleagues, experts, Microsoft Cloud Advocates, Program Managers and technologists at the event it offers excellent networking opportunities.
I will be around at the VIP Cloud Party, which provides plenty of networking opportunities and the chance to chat to the presenters and your peers. On top of that, I will be available between sessions and the “Ask The Experts” (ATE) speaker booth.
If you have questions about Hyper-V, Backup, Storage, Networking and best practices do come and find me. I don’t know it all, far from, but I have been able to help out many people before at conferences. Whether you work in small, medium or enterprise-sized organizations it’s free to ask and the worst that can happen is that I don’t know. I have a sweet spot for RDMA and PMEM, so if you ‘d like to chat, come find me!
Join us in Prague at Ask The Experts Europe
I hope to see you in wonderful Prague at a great conference! I am looking forward to meeting you there and presenting at Experts Live 2019 Europe in Prague. You can make new friends and catch up with others while you educate yourself. That’s a great deal.