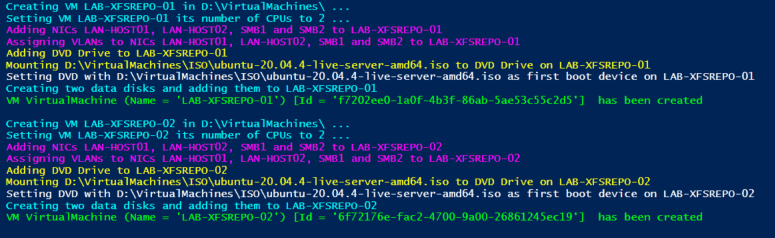
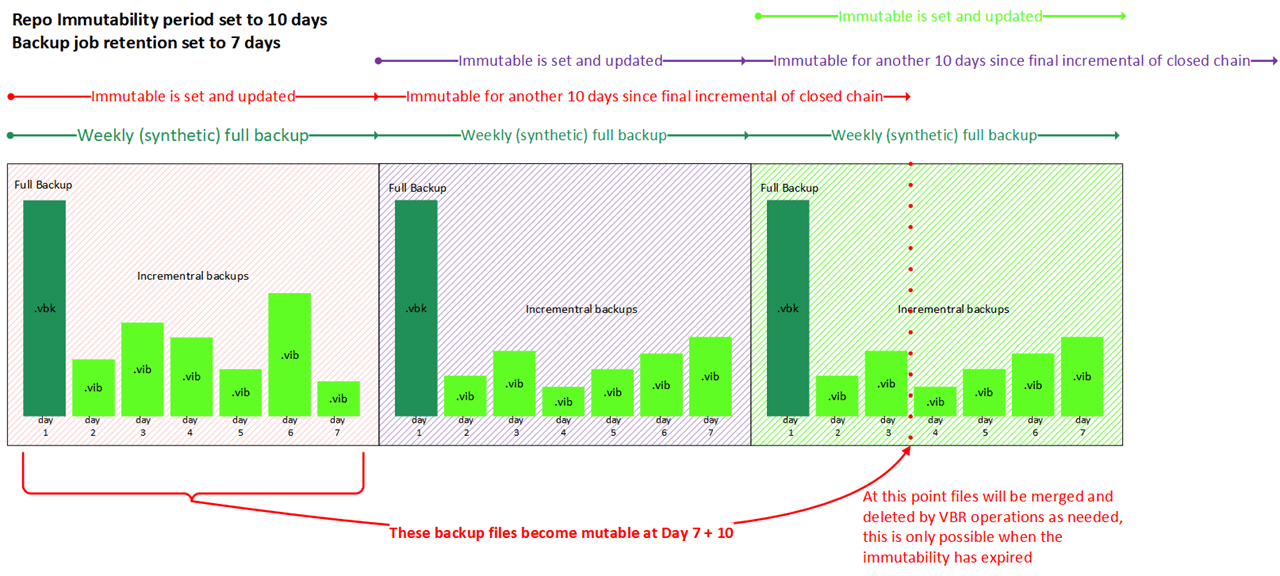
Why attend VeeamOn?
VeeeamOn 2023 – The Community Event for Data Recovery Experts is in less than 50 days. During May 22nd -25th 2023, Veeam is organizing a hybrid event in Miami, Florida, USA. You can attend in person or online. This is “The Community Event for Data Recovery Experts” so if you fall into that target group, try to be there!

The high-level agenda is already available as well as the speakers list. A detailed agenda and schedule will be available any moment now. As you can see the content is real world actionable content. You will learn concepts, get tips, gain a deeper understanding of the challenges you face. Next to that you will learn how to address those challenges from industry experts and fellow professionals. Yes, it is not just vendor driven. The event speakers include partners, fellow IT professionals at customers sharing their knowledge and expertise with you!
This is truly a community event, and it will help you expand your on-prem, hybrid, cloud and security skills when it comes to data recovery. You will learn to build better solutions while growing your professional network in the global community.
VeeamOn is really special!
What sets Veeam apart is how accessible their top talent and leadership is. I have experienced it firsthand. That’s why I have found memories of the times I attend VeeamOn or other Veeam events. Parts of that is the conversations I had with Anton Gostev, Danny Allen, Rick Vanover and their team members. All solid technologists with a no nonsense, straight talk attitude when it comes to our business and technical challenges. This is pretty unique and shows how much they are involved in guiding Veeam on the best possible course to serve their customers as well as possible! I would say it is a privilege, but to Veeam each of their customers truly matters. How do I know? I am one and Veeam is a beacon of light and hope for other vendors to follow.
Call to action
Register now for VeeeamOn 2023 – The Community Event for Data Recovery Experts and do not miss out! Because I am a Veeam Vanguard and as gift to my readers and followers Veeam provided me with this discount code VOMIAMI1002. Using it will give you a 100$ discount when registering. I really hope you can make it, if not in person, then at least online. The good news is that Veeam got pretty good at organizing online events and makes those interactive as well. I wish you a great conference!