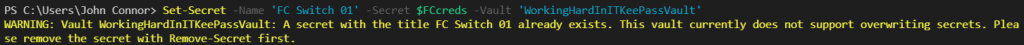
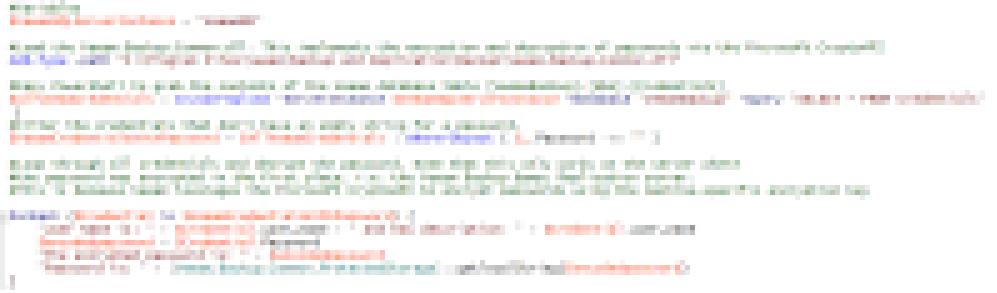
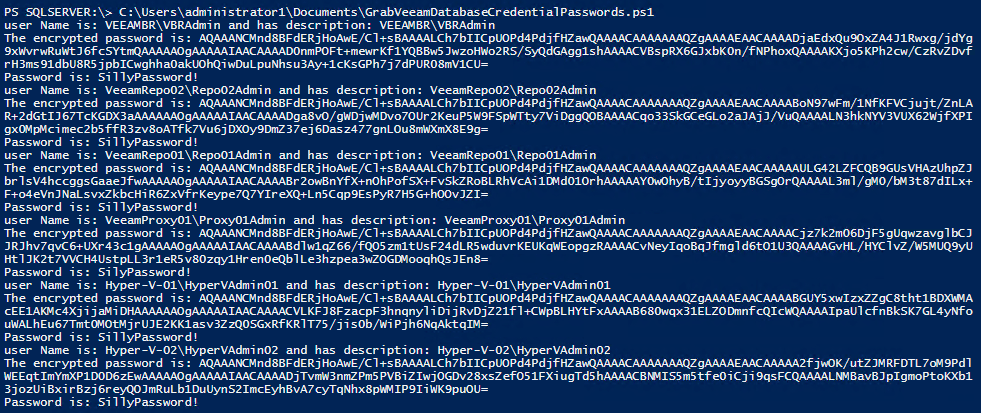
FEITIAN FIDO2 security keys
I requested a lab trial sample of some FEITIAN FIDO2 security keys as they offered them to interested and qualifying parties for testing purposes. I was interested in their biometric security keys. So I reached out to see if I qualified, and they sent me two securities for testing in the lab. One is the K26 BioPass FIDO2® with a USB-C interface, which has, you guessed it, biometrics, meaning fingerprints. The other one is the iePass FIDO® with both a USB-C and lightning interface. This one has no biometrics but works with touch and makes a good choice for Apple devices. Now, the focus for these security keys is most often professional use cases. Still, I also wanted to point out that you can leverage a security key for your personal online accounts.
Yes, you as an individual should also be serious about protecting your online presence. For many of us, if not most, our smartphone is the primary MFA device we use. But I am also interested in an alternative.
FEITIAN
FEITIAN has a wide range of FIDO2 security keys for the many different needs and budgets out there. For me, biometrics is a must for the best possible security. However, they also offer other models, including versatile FEITIAN FIDO2 security keys that offer multiple interfaces like USB, NFC, and Bluetooth. That makes them more widely employable, but as said, I am focusing my efforts on biometric capable ones.
When it comes to biometrics, FEITIAN is the first to offer me that capability. Hence they caught my interest. In addition, ad far as I know, FEITIAN was the first vendor to achieve the FIDO Biometric Component Certification on April 29, 2021. That is a requirement to qualify for FIDO Level 3 and higher Certification. Next to that, they are very responsive to my communications and feedback. So far, so good! I know of one other vendor that has biometric FIDO2 keys available, that’s TrustKey. I know Yubikey has had them coming but so far they are not available.
Why a FIDO2 security key?
I usually use a smartphone as my primary MFA tool. A smartphone offers push notification MFA challenges that are easy to approve, allows TOTP code to access services, and can receive single-use passcodes via SMS or e-mail. On top of that, a good smartphone is fingerprint protected. That is a lot of flexibility on a single device most of us carry around daily anyway.
Redundancy for your smartphone
You can use a second smartphone for redundancy, but I use a FIDO2 security dongle where possible. I hang it on my key chain, and even when I merely forgot my phone that day, I have the security keys as a second option handy. That is far more likely to work than counting on having that second phone in my pocket.
So why use a FIDO2 security key? Well, firstly, when using MFA, and most certainly when going ultimately passwordless, you need a second way of accessing your account. I don’t just mean your emergency recovery key or such, but a backup device to answer your MFA challenges. I do this just in case you forget or lose or damage your smartphone or FIDO2 security key and can’t wait for all that to be fixed, replaced, and otherwise handled.
FIDO2 keys as primary and backup MFA solution
Secondly, sometimes FIDO2 security keys are the primary choice, depending on the variety of organizations’ needs, processes, and approaches to dealing with MFA.
Biometrics
I prefer security keys with biometrics. Together with their PIN code, the registered fingerprints provide a device that remains very secure, even when lost. It is also still secure when you leave the security key on your device. Merely touching it is not enough. The fingerprint needs to match even when your device or service does not prompt for your PIN. That keeps your kids or colleagues out of your accounts when you are not around. Secondly, you can register the fingerprints of another person you trust. That comes in handy if access is needed and you are incapacitated. A use case for this is for break glass accounts to Azure, for example.
Where to use FIDO2 security keys?
People use FIDO2 security keys most often to secure applications, services in professional settings (Azure AD, O365, websites of various professional services, etc.). That said, I use them for my personal security needs as well where ever I can. They are my second MFA device next to my smartphone. I like them, and I promote them to friends and family as I explain to them about MFA and the passwordless future. Yes, I do that. It is a requirement. That requirement materializes as mandatory security training when they dare ask me to help them select a new laptop or computer.
So in a few upcoming blog posts, I will discuss how to set them up and use them with various personal and professional services. Think about Microsoft’s Outlook, Teams, OneDrive, and services like Twitter, my WordPress blog, and my personally hosted IAAS VM for RDP or console access.
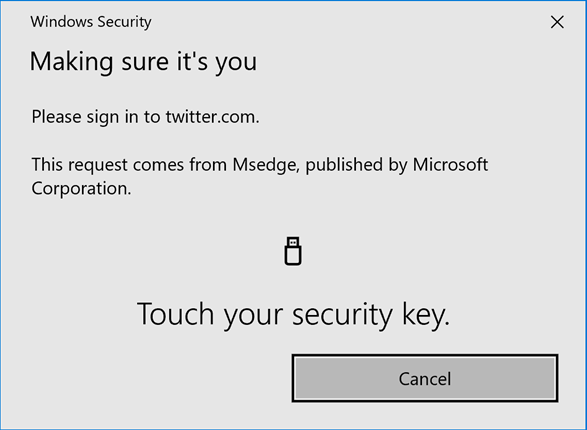
You can also use them with your client device or on a server with the right MFA provider or security vendors software and protect access when services like Windows Hello are not available to you for whatever reason.
I have found the FEITIAN FIDO2 security keys easy to use and to work reliably. In addition, they appear to be of high quality and solid enough to survive on my keychain.
Mind you, you cannot use a FIDO2 security key everywhere yet, which I find a pity. It shows security still has some work to do. But, where I can use a FIDO2 security key in combination with a smartphone authenticator app.
No matter what, use MFA wherever you can
Remember that with MFA, you are far less likely to become a victim of unauthorized access to your clients and services. It makes so much sense it should be the default for everyone today. It is an essential step on the road to an actual passwordless world in a zero-trust environment. We are getting closer to that world as recently, Microsoft allows you to remove the password from your personal Microsoft account when you have MFA in place.
Disclaimer
FEITIAN did not sponsor me or otherwise reward me for writing this blog post. However, they did provide me with the two FIDO2 security keys, which I appreciate as it helps me test and show scenarios in the lab and at presentations. For that, I would like to thank them.