Windows 10 build 10240 has been released to the Fast Ring. That’s what I’m running on my laptops now. There were heavy rumors yesterday that this is the to Release To Manufacturing (RTM) build and is the one to be publically available on July 29th. But there is no hard confirmation on this by Microsoft yet Build 10240 now available for Windows Insiders in Fast and Slow rings.
“Over the past few days we’ve been preparing our release pipelines and processes, and this build is one step closer to what customers will start to receive on 7/29 …
On Monday we announced that builds from here on will only be available through Windows Update, so to get this one you can either wait and it will be installed automatically.”
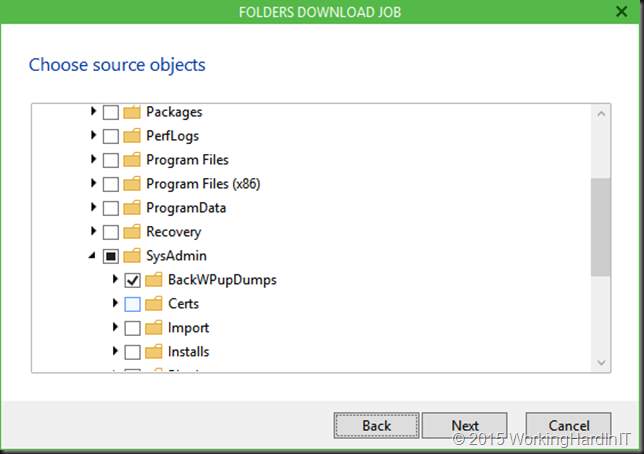
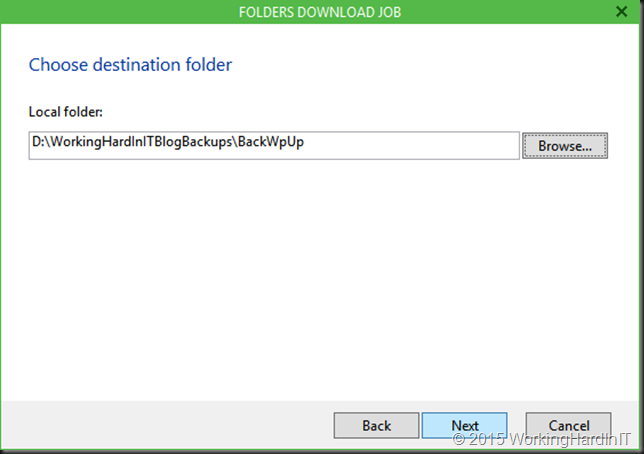
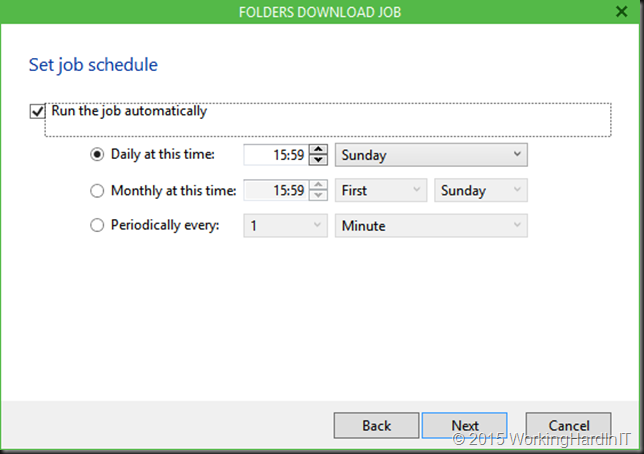
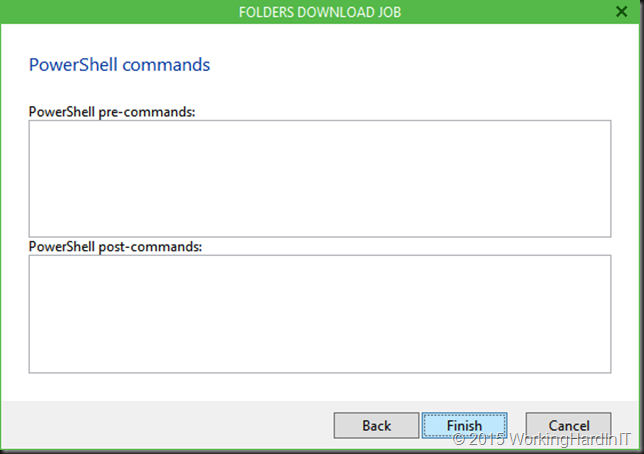
Here’s how you prepare to roll it out in your company.
In a previous blog post I wrote about the update you needed for your KMS server to be able to activate Windows 10 clients. Read about that in KB3058168: Update that enables Windows 8.1 and Windows 8 KMS hosts to activate Windows 10 You can get ready today, you have all you need.
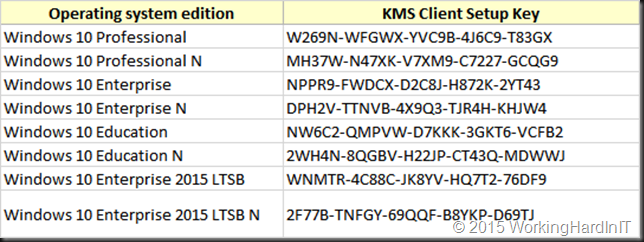
Meanwhile Microsoft has also published the Windows 10 client KMS activation which keys can be found here Appendix A: KMS Client Setup Keys
Do note this is the key you use when you activate the Windows 10 Client against a KMS server. It is not the KMS license server key. That one you’ll need to obtain from your valid Microsoft licenses.
If you don’t have a KMS, the MAK key option will still be available.
Windows 10 looks set for a great start. DELL has been accepting preorders for a month now (Dell Brings Windows 10 to Life: Pre-order Today) which will be shipped to you on July 29th. Windows 7 owners could already reserve their upgrade via Windows update. The OEMs and the customers seem ready. I’ve heard of several large deployments in the works, often from organization still running Windows XP. We’re a Windows 8.1 shop but our new images are being build and will be deployed as the default image via MDT. We won’t let our investment in software assurance go to waste ![]()