KeePass SecretManagement extension vault
The SecretManagement and SecretStore can work with SecretManagement extension vault modules. These can be found in the PowerShell Gallery using the “SecretManagement” search tag. Some example are:
I use KeePass and as such, the KeePass SecretManagement extension vault is the one I will demonstrate. First of all, install the module. Note that I chose to use the most recent beta version, which is 0.9.2-beta0008 at the time of writing this blog post.
Install-Module -Name SecretManagement.KeePass -AllowPrerelease
Naturally, if you haven’t installed SecretManagement and SecretStore modules yet, you must now really do that to be able to play with them.
Install-Module Microsoft.PowerShell.SecretManagement, Microsoft.PowerShell.SecretStore
Now that has been taken care of we can start testing the KeePass SecretManagement extension vault.
Using the KeePass SecretManagement extension vault
I created a demo KeePass .kdbx file in which I stored some example user names with their passwords. This file has a master password. You can also use a key or the Windows user account if you want to do so.
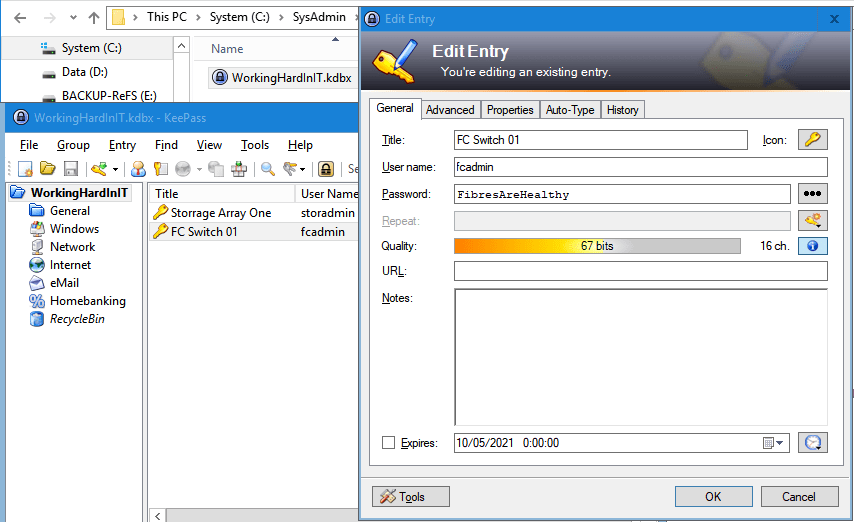
Now I will register the KeePass file as a Vault
Register-KeePassSecretVault -Name 'WorkingHardInITKeePassVault' -Path 'C:\SysAdmin\Authentication\workinghardinit.kdbx' -UseMasterPassword
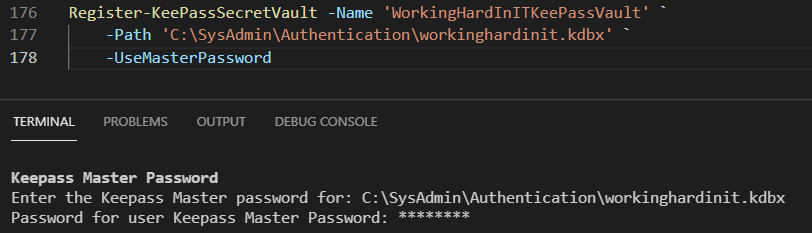
As you can see this prompts you for the KeePass Master Pasword.
Keepass Master Password
Enter the Keepass Master password for: C:\SysAdmin\Authentication\workinghardinit.kdbx
Password for user Keepass Master Password:
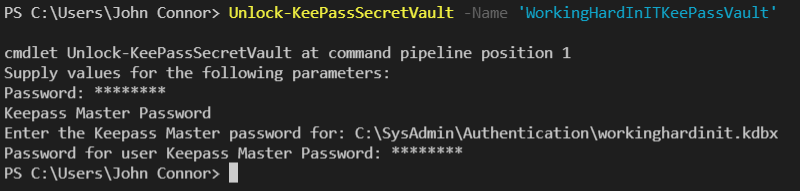
Now that is done, I will unlock the KeePass secret vault so I can use it in automation without being prompted for it. By default, it remains unlocked for 900 seconds (15 minutes). This is configurable.
Unlock-KeePassSecretVault -Name 'WorkingHardInITKeePassVault'
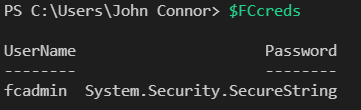
$FCcreds = Get-Secret -Name 'FC Switch 01' -Vault 'WorkingHardInITKeePassVault' $FCSwitchUser = $FCcreds.GetNetworkCredential().UserName $FCSwitchPwd =$FCcreds.GetNetworkCredential().Password write-Host -foregroundcolor Green "FC Swicth 01 username $FCSwitchUser has $FCSwitchPwd for its password"
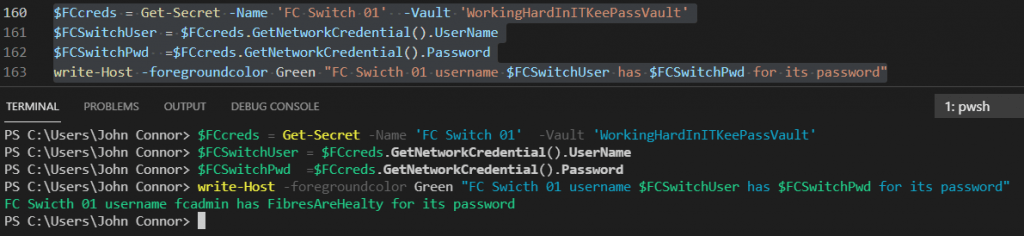
Note that the entry for the secret is a network credential. As result, we can use the properties of the credential object to obtain the username and password in plain text. That is to say, we can (and should) use the credentials directly. You do not need to show or use the password in plain text. I did this here to show you that we got the correct values back.
Updating and adding secrets
Currently, updating the secrets with is not supported.
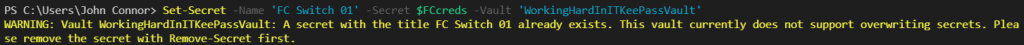
We need to first remove the existing one for now and re-enter the information. We’ll see how this evolves
Remove-Secret -Name 'FC Switch 01' -Vault 'WorkingHardInITKeePassVault' $FCcreds = Get-Credential -UserName 'fcadmin' Set-Secret -Name 'FC Switch 01' -Secret $FCcreds -Vault 'WorkingHardInITKeePassVault'
Finally, the good news is that there is also a PowerShell KeePass module that you can use for that sort of work. So you have the means in PowerShell to do so. See Getting Started · PSKeePass/PoShKeePass Wiki (github.com).
Conclusion
That was fun, was it not? The SecretManagement and SecretStore modules are going places. I hope this helps and happy scripting!
