Because hope don’t float!
This is part 1 of a series on IT Strategies. Just some musings. You can find Part 2 here: https://blog.workinghardinit.work/2010/08/14/it-strategies-from-window-nt-3-51-to-the-cloud-era-part-2/
Not many people I meet in businesses seem to be able to define “ICT strategy” without playing some sort “Bullshit Bingo” I’ll give you my opinion. During my years in IT I’ve read and thought a lot about the value of what we design and build. What you’ll find here stems from well over a decade of reading, thinking, working, discussing and helping to develop IT Strategies with colleagues, businesses and consultants whilst exploring ways to deliver value through ICT. One thing I should perhaps add that I have never been in a sales role, so this is not from an account manager’s perspective. But I do recognize and accept that everyone whatever his or her function has a “sales” role in order to be allowed to execute ones proposals. I owe a debt of gratitude to so many people over the years who have helped shape my vision on IT. There are so many voices and opinions, some I agree and some I disagree with, that have influenced my ideas, that in the end all of what you read here is a collection of all those opinions combined with my interpretation of them. Part 1 is about where IT strategies fit in and why they are. Part 2 will address my opinion on how to achieve them.
Introduction
The reason you hear more and more about strategic IT and commodity IT in recent years is due to the attention cloud computing is getting in the media. One of the main forces driving the cloud computing business is economic pressure and the need to provide affordable, scalable IT in a commodity market. Combine this with the “discovery” of business and IT alignment by main stream management and the “strategic” plans will flow abundantly. They’ll almost certainly throw in an “IT needs to learn it’s here for the business needs”. What does that really mean? That management is not capable of using IT for its business needs and allows money to be wasted. Whose responsibility is that? What if they let the same happen between financials and sales? In my humble opinion main stream business managers urgently need to make the effort to learn about the realistic use and benefits of IT. A divide between business and IT is a manmade artifact and not something natural, it is a result of management failure. Bar the stereo type nerds, I see more efforts of IT managers & architects to think business minded than by main stream management in thinking about using IT as a true competitive differentiator. Once the words economy and competition are in play you start talking strategies, just like the military. That’s not a coincidence. Take away the niceties and business is a non-lethal form of warfare. I guess that’s why “The Art of war” was or is such a popular book in top business circles. Just do an internet search for “The art of war business strategy”. The correct definition of what strategy means is out there in plain sight for all of to read and learn.
So why is it that when talking about strategies, ICT related or otherwise, you rarely get a solid response that truly addresses the subject? People seem to mistake simple long term planning and goals for strategies. Plans are used to realize strategic goals; they do not define a strategy. A strategy is what you will do to out flank your competitors to gain an advantage. That advantage, in today’s world, means being different and good. It is almost certainly not about being the best. What is best depends too much on the unique situation of every organization, its specific needs and circumstances at that moment in time. It’s indeed all rather fluid and dynamic, so “best” is very time limited. Anyway you’d better have something that differentiates you from the competition in a positive way. Otherwise there is no compelling reason to become your customer.
Why is having a unique approach and being good at it so important? Being the same as anyone else makes you plain, a commodity that’s readily available. If on top of that your customer’s service sucks, you’ll start losing customers as no one is willing to pay for that. This drives down prices even more and robs you of all potential benefits of any unique selling points you might have. That is far from competitive. Unless your aim is to become king of low priced, bulk delivery for a product that doesn’t require services whatsoever that’s a bad strategy and even then you will have to be better than your competitors in that particular playing field. You have to stand out somehow.
Also, a strategy has to be correct and honest. False assumptions, self-deception, faking and lying as in “methodology religion” will make you lose all professional credibility with your personnel and investors. Once you’ve sunk to that level there is little or no hope of ever recovering from that position. You really cannot get away with faking a strategy.
So what is “my” strategy as an infrastructure guy in a business world to make sure that we are different and good? Well, you already read the appetizer, now read on to find out. And believe me, you need to find out! Way too many business & IT strategies are esoteric boardroom level documents that have little or no correlation with the reality in the trenches. They are made to have some checkboxes ticked on an audit report or are actually just plans with not strategic content what so ever. Sometimes you really wonder why they even bother making them. At least they could have avoided wasting the time and effort.
Defining how the ICT strategy relates to the business strategy
Before we can define what makes a good ICT strategy we need to talk business. It needs to be a part of the strategic business plan or you shouldn’t even bother having one. Oh, and by the way, if you don’t have a high quality business plan made by and supported in actions by knowledgeable, passionate, driven, motivated and hardworking management, walk away. No good ICT strategy will ever come from such a situation. Buying technology cannot fix organizational problems. Please repeat this last sentence at least three times out loud. You need to hear it and let the message sink in! In such a situation having an IT strategy is the least of your problems.
We already stated that a strategy is about distinguishing you from your competitors. This can mean many different things depending on the circumstances. Better products, the same product but with better services, cheaper but good enough for its purpose, etc. Be brutally realistic. If what you do does not set you apart from your competition in a positive way, you have no strategy or have been ill advised on what constitutes a strategy. The fact that “no one else does what we do” is not a strategy, it will not last! The fact that people are obligated to use your services by law is not a strategy. It might be a short term advantage, but it creates no good will with your customers, especially not if your services or products are mediocre or bad. And please be more than just be the odd one out, sure you’re different but that’s not the different you’re looking for.
You must also realize that strategies have a limited shelf life. Sooner or later your competitors will realize what your strategy is and if it works they will start copying it. More often than not they will add some improvements having the benefit of 20/20 vision through hind sight. This means that, over time, what was once a distinguishing solution that gave you a competitive advantage becomes a mere main stream commodity. Now please realize that being a commodity does not mean irrelevant or useless. Power, heating, fuel, telephones, e-mail, storage, file servers… are all commodities we cannot do without! But in the commodity sector you will compete by being different in pricing, quality of services and added value. Only when technology becomes a blast from the past by significant advances or changes in science it becomes economically useless. Think steam engines … but … retro does exist and come backs do occur. Windmills any one?
I know the cloud hype recuperates just about everything that is delivered can be over the internet and is service oriented but please realize that not all commodities are or will be services.
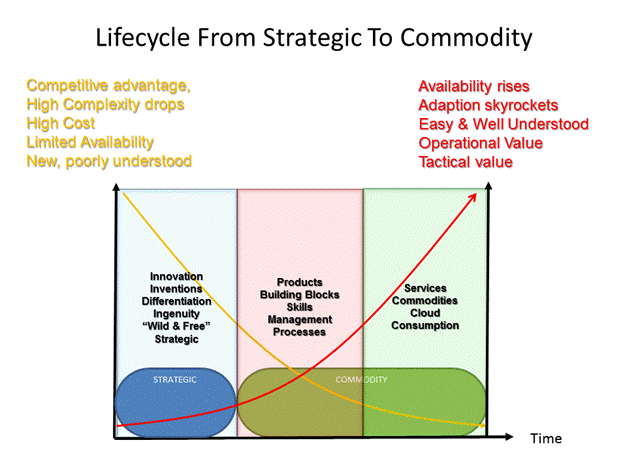
Given the fact that strategies are far from long lasting entities, what does this mean for an IT strategy? Simply put: speed and agility are of the essence. We must be capable of moving fast and decisive. There is no time anymore for years of thinking, contemplating and testing. The long term vision must still exist and it is extremely important, but it is not the same as a strategy. To reap the benefits of long term thinking one needs to survive long enough to be around! 15 year long term strategies are doomed. These are day dreams. A bit like the Maginot Line the French build for over a decade but was utterly useless as its concept was out of date by the time World War II broke out. Long terms visions are realized through several sequential and adaptive strategies. As you can see in the figure with time strategic solution becomes a commodity and a part of the IT infrastructure that needs to be maintained. A good strategy takes this into account so that the strategic solution can evolve into an operational and tactical commodity instead of a very expensive drain of resources.
One could say that all IT can be found somewhere between following states:
· Strategic: Technology that differentiates us in support of (new) business strategies. This is what makes us more competitive, that adds value, because it’s unique and innovative.
· Commodity: Stuff we need but no longer adds competitive advantage. It does provide tactical or operational benefits and you can’t do without them. Make note, strategic commodities exist, oil is a prime example, water another one. So commodity is not a synonym for low value, it just doesn’t add value in itself or no longer serves as a differentiator.
Everything else, whether it is cheap or expensive, subsidized or self-sustaining are frankly technology hobbies (not in the picture). Where are the value and the profit? Management should avoid this. The best thing that can happen here is that you actually learn something building & maintaining it or use it as a lab for creative innovation. But that’s not a hobby anymore … that’s a dream job for engineers.
Tell me what an ICT strategy is already!
An ICT strategy supports the business initiatives that provide a competitive advantage to an organization in such a way that it does not become a pain in the ass over time. Only incur technology debt where and when needed and manage it carefully. But how the hell does that materialize in reality you must be wondering by now? Well it is the combination of creatively building, deploying, operating and using solutions that deliver value by making you more competitive. Solutions scan be realized using standard software and hardware, with custom build applications or a combination of both. Whatever the case … the solution requires very knowledgeable people, serious skill sets, a mind driven by curiosity and the need for results.
People buy results, not services or efforts. This is one of the big mistakes in the thinking of many modern so called service driven companies. They fail to provide good services, let alone results. They are in effect just low cost / low value operators. If you provide services they need to be there to produce the results. Otherwise you are, for all practical purposes and intent, lying which will come back to bite you. Take note however that too much service is financial suicide. Don’t cater to individual and unique needs unless that is your core business.
Since solutions are custom build on development platforms and infrastructure it is critical to realize that the choice of platforms and infrastructures can mean the success or failure for an organization since it directly relates to its ability to compete. Yes, once again, the reason for having a strategy in the first place!
The most common issue we see when dealing with an IT strategy is that many organizations have no clear picture about what they do, how and why. They just seem to do “stuff” and expect of rather hope that hard work and effort will help them realize their goals. But without clear and well defined goals there is no way of achieving them. Efforts and hard work alone will not produce results. Customers do not pay for hard work, they do not reward efforts. That was something that worked in kinder garden but fails in a business environment. Remember, customers pay for results. You cannot buy a product that will deliver these out of the box.
So what must an ICT strategy achieve?
Since we have seen that strategic solutions eventually become commodities, any combination of infrastructure, platforms and solutions must work well during their entire life cycle. Decisions that focus only on strategy might lead to the implementation of the latest and greatest technology. This can lead to very divers, esoteric and heterogeneous environments with very high integration & support costs. It also incurs the cost of finding, retaining and maintaining good developers and engineers with knowledge about such systems.
On the other side of the equation one can not only worry about keeping short- and long-term support costs low. This will lead to missing out on the business benefits that new technologies can bring. In the end finding the right balance between these two is very important and failing to do this will be very costly in financial repercussions, lost opportunities and failed projects. This ends in the downfall of the organization since it becomes irrelevant in the market and has no more means to support itself.
Custom build solutions do not exist in isolation. They need to run on an infrastructure, connect to other systems, be able to be secured etc … This is called integration and if this is overlooked it can become a financial burden that negates the added value of an IT solution and make it a cost instead of an asset. For example “Best of breed” has often failed in the sense that is did not deliver enough value to justify the high cost of acquisition, maintenance and integration. The real killer here is the efforts and thus cost involved in integrating all these. Even if you do get it to work it is often in a way that negates good practices, reduces security and incurs a high, cumbersome administrative overhead which is error prone and expensive. It does make a good revenue stream however for “consultants”.
This is part 1 of a series on IT Strategies. Just some musings. You can find Part 2 here: https://blog.workinghardinit.work/2010/08/14/it-strategies-from-window-nt-3-51-to-the-cloud-era-part-2/

![clip_image002[5] clip_image002[5]](https://blog.workinghardinit.work/wp-content/uploads/2010/08/clip_image0025_thumb.gif)