Activating Windows Server 2016
So it’s time to make sure we start thinking about activating Windows Server 2016 in our environments.
If you manage on premises environments with one or more AD domains or even forests you might be in a situation where Active Directory Based Activation (ADBA) is the easiest solution. If you set this up you’ll enjoy automatic activation of the OS after joining domain configured with ADBA. This is what I use for the Office and Windows editions that support it. It’s fast and easy to set up.
Now when you’re hosting IAAS services this might not be your best approach as that means it will need to be set up in the AD of your tenants. Something your most often don’t manage or control if an AD is even present. You also need the right versions of both AD and client software and operating systems to use this. That can also be an issue on premises. But don’t worry. Both Key Management Service (KMS) and Automatic Virtual Machine Activation (AVMA) will work for IAAS and for on premises in these situations.
I actually support 2 on premises environments where ADBA is being used for the recent OS and Office versions while KMS is still around for the older OS versions. That way as the old OS versions are phased out the KMS infrastructure can be retired as well.
KMS Server activation
You can use a Windows Server 2012 R2 or 2016 server as a KMS server. I just made sure my KMS server was fully patched before I attempted to install and activate the Windows Server 2016KMS key. That means that on Windows Server 2012 R2 you want KB3172614 installed as this enable support for Windows Server 2012 R2 as a KMS server host to activate Windows Server 2016. See https://support.microsoft.com/en-us/help/24717/windows-8-1-windows-server-2012-r2-update-history. For Windows Server 2016 this means don’t do anything unless you have all the zero day patches installed.
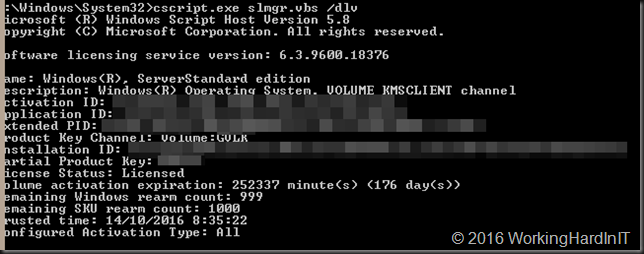
First we take a look at the current situation by running slmgr.vbs /dlv
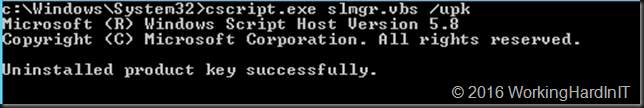
Uninstall the current KMS key using slmgr.vbs /upk, please use an elevated command prompt 
Now you can install the new Windows 2016 KMS key on your KMS server. If you run in to any issues here, restarting the KMS Service can help ((“net stop sppsvc” and “net start sppsvc“) . Try that first.
slmgr.vbs /ipk JOINT-THENA-VYBOY-SNOCR-ACKS!
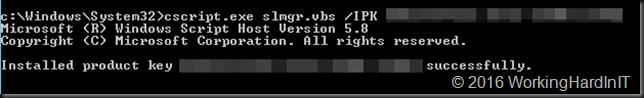
The key listed here is for all you wannabe pirates out there, sorry, this is the navy. If you’re, looking for illegal keys, cracks, keygens, activators or dodgy KMS virtual machine for Windows activations and such this is not the place  .
.
If you now run slmgr.vbs /dlv you’ll see that the license status is “notification” as the server hasn’t been activated yet.
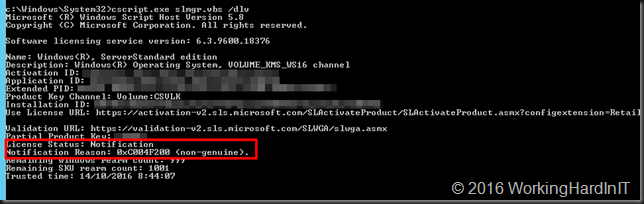
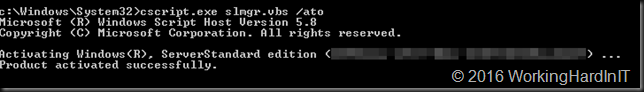
You now need to activate your server with the KMS key first by running slmgr.vbs /ato
We can now look at what’s installed now by running slmgr.vbs /dlv again. As you can see we’re in business to activate all our Windows Server 2016 and any OS version below that if t supports KMS activation.
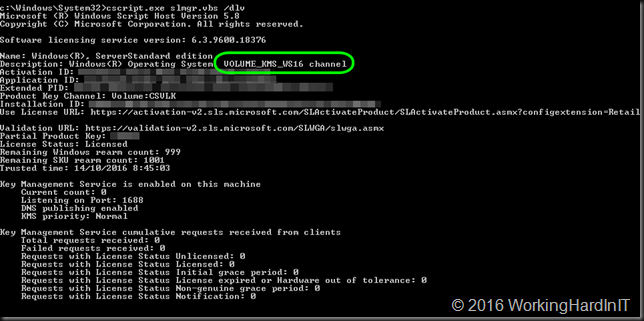
Now in Windows 2012 R2 and later we also have the Volume Activation Tools feature you can install and use to do this, just like you use this for the ADBA setup.
Activate guest VMs on Hyper-V hosts
Configure Guest VMs activation with AVMA
If you’d like to leverage AVMA, which is especially handy as a IAAS hoster, you’ll need to use Windows Server 2016 or 2012 R2 Datacenter on your Hyper-V hosts and activate them by your chosen method (MAK, KMS, ADBA). You also need to use Windows Server 2016 or 2012 R2 Standard/Datacenter in the guest VMs. As long as your Hyper-V hosts is activated, every new guest deployed on them will be activated automatically. That’s it. There’s no need for a KMS or ADBA configuration for the guest (tenant VMs) or even an internet connection. The later is great for more secured environments. Easy peasy.
The only thing you need to do is use the AVMA client key in the slmgr /ipk. These are public ones actually just like the KMS clients keys.
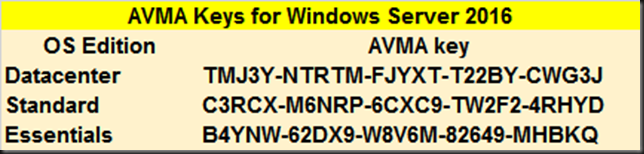
There are two things to note: The first,a s you can read in the link to the AVMA documenation above:
“AVMA requires a Microsoft Virtualization Server running Windows Server 2012 R2 Datacenter or Windows Server 2016 Datacenter. A Windows Server 2016 AVMA host can activate guests that run the Datacenter, Standard or Essentials editions of Windows Server 2016 and Windows Server 2012 R2. A Windows Server 2012 R2 AVMA host can activate guests that run the Datacenter, Standard or Essentials editions of Windows Server 2012 R2.”
This means a Windows Server 2012 R2 Host cannot activate Windows server 2016 VMs. You can upgrade “cheaply” that way, let’s put it like that.
Secondly make sure the VM has Data Exchange turned ON in Integration Services. That’s the mechanism leveraged to make AVMA work. You should have that on anyway, really, I mean it 🙂
Configure Guest VMs activation with KMS
The public client KMS keys for VLK media can be found here: Appendix A: KMS Client Setup Keys I’ve only included a screnshot of the Windows Server KMS client keys here. More info is in the TechNet page.
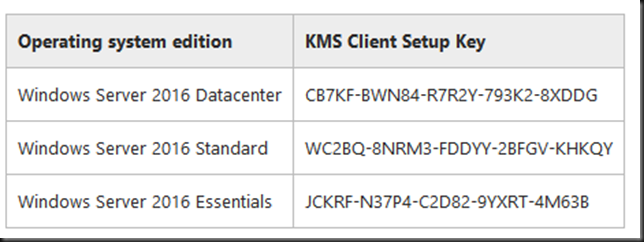
To make sure a Windows Server 2016 Datacenter VM can activate via a KMS serer install use the below commands to replace a MAK key for example:
slmgr.vbs /ipk CB7KF-BWN84-R7R2Y-793K2-8XDDG
slmgr.vbs /ato
NOTE: all these keys can be used within a template or via unattented installation config files.