MFA for a highly available RD Gateway
Recently I decided to write up a couple of articles on how to set up MFA for a highly available RD Gateway. Why? Because so much information on the internet is fragmented and as such incomplete. So I wanted a reference document for myself. As I was making that document I realized I needed to explain the why and not just the how. The “why” is what helps people support and troubleshoot the solution during its life cycle.
The above, in combination with me being a verbose son of * led to 44 pages of information. So, I decided to publish it as a two-part article series.
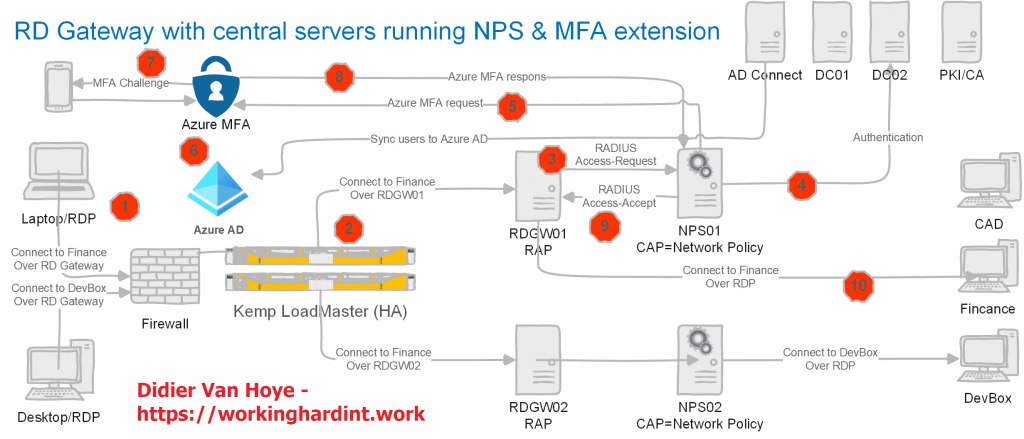
You can find the articles here Transition a Highly Available RD Gateway to Use the NPS Extension for Azure MFA – Phase I and Transition a highly available RD Gateway to use the NPS Extension for Azure MFA – Phase II
Why and when should you read them?
If you have RD Gateway running and you have no MFA solution set up for it, I highly recommend you head over to read these two articles. That is especially true when your RD Gateways solution is a high availability (HA) deployment with an RD Gateway farm behind a load balancer. In that case, you want your MFA components to be HA as well! For some reason, so many guides on the internet ignore or brush over HA very cavalierly. That is one thing I hope these two articles remediate.
Next to that, it has many details on every aspect of the deployment to make sure you get it up and running successfully and correctly.
Finally, I present you with a collection of troubleshooting information and tools to help you figure out where the problem is so you can find a way to fix it.
That’s it. I really think it can help many of you out there. I hope it does.