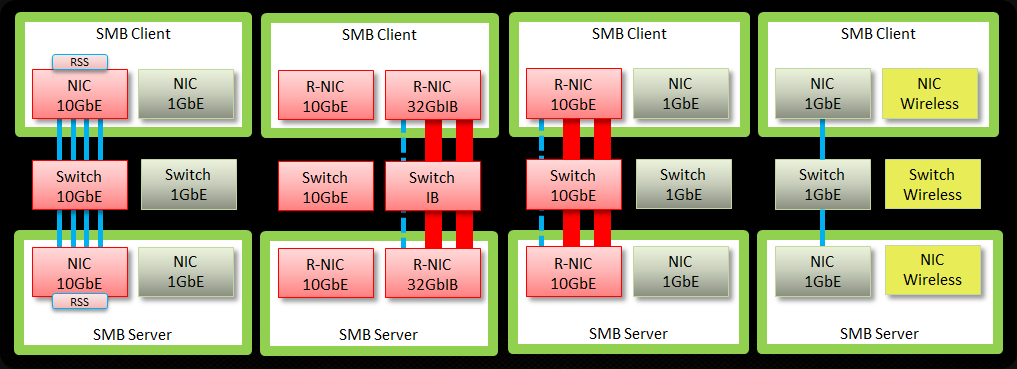
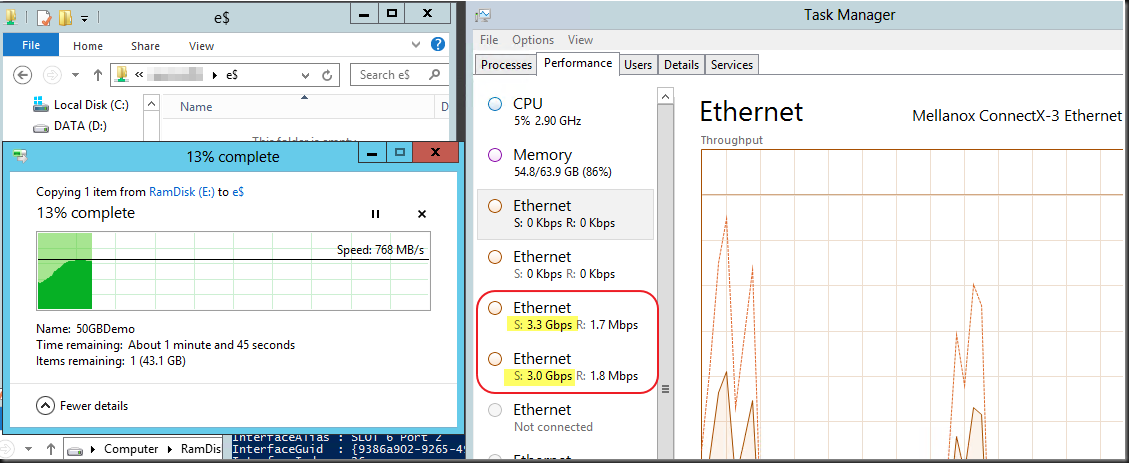
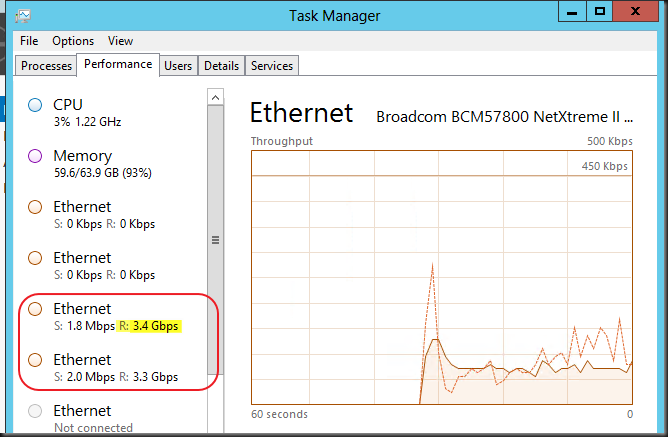
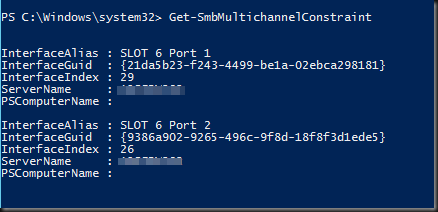
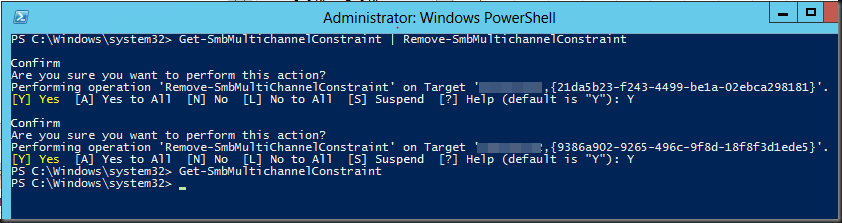
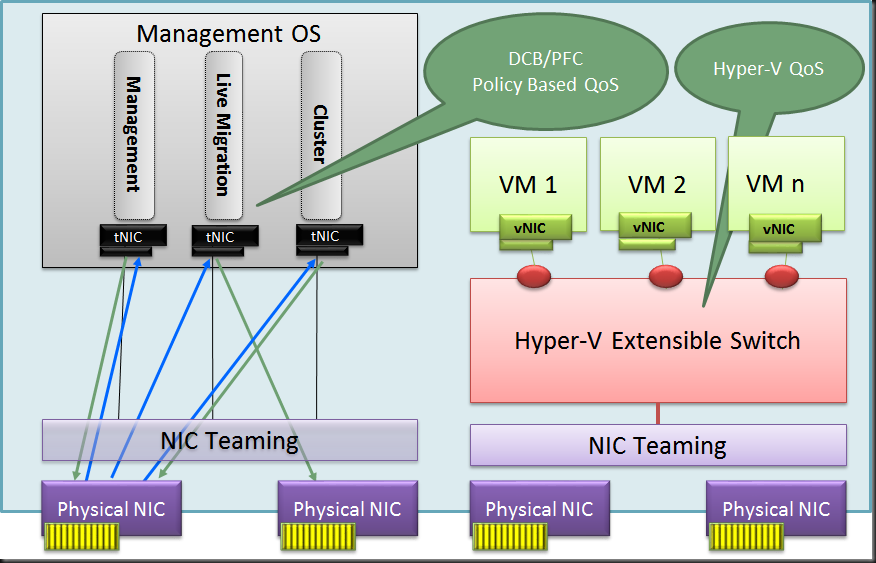
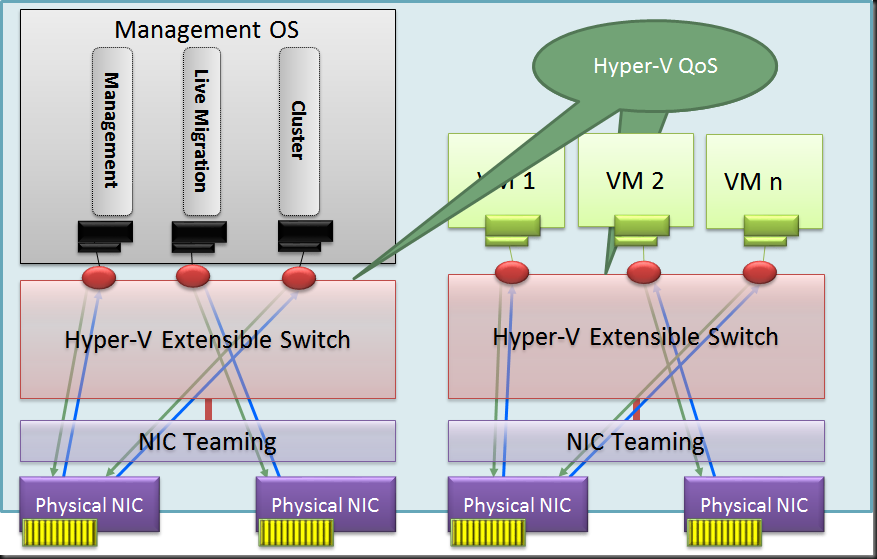
I’d like to chime in on a recent blog post by Aidan Finn Hey Look–Your Business Is Running On A 10-Year Old Server Operating System (W2003). The sad thing is this is so true and “the good” thing is some are even still on Windows Server 2000 so even in worse shape. Now I realize that not all industries are the same but keeping your operating systems up to date does have it’s benefits for all types of companies.
- Security Improvements
- Improved, richer, enhanced features
- New functionality
- Support for state of the art hardware & software
- Supported for that day the SHTF
- Future Proofing of your current investments
For one, all the above it will save you time and money. On top of that mitigates the risks of lost revenue due to security incidents & unsupported environments no one can fix for you.
Think about it, if you’re running Windows Server 2000 or 2003 chances are you are paying for software to provide functionality that’s available right out of the box. You’re also putting in the extra effort & jumping through loops to run those on modern server grade hardware.
You’re also building up debt. Instead of yearly improvements keeping your infrastructure & services top notch you’re actively digging an ever bigger, very expensive, complex and high risk hole where you’ll have to dig your self out off. If you can, that is. Not a good place to be in. Still think leveraging software assurance is a bad thing?
So while way to many companies now have to assigned resources to mitigating that looming problem we’re focusing on other ventures (such as Hyper-V, Azure, Hybrid Cloud, …) and just keep our OS up to date at a steady pace, like before. Well people that doesn’t happen by accident. We’ve maintained a very healthy pace of upgrading to the most recent version of windows in our environments and at times I have had to fight for that and I’m I will again..But look at our base line, even if the economy tanks completely we’re in darn good shape to weather that storm and come out ahead. But it’s not going to happen by sitting there avoiding change out of fear or laziness. So start today.A point where I agree with Aidan completely: if your “Zombie ISV” and other vendors are telling you Windows 2003 is great and you shouldn’t use those new unproven versions of the OS; they are really touting BS. They have fallen behind so far on the technology stack that they need you to stay in their black hole of despair with them or they’ll go broke. Just move one. Trust me, they need you more than the other way around