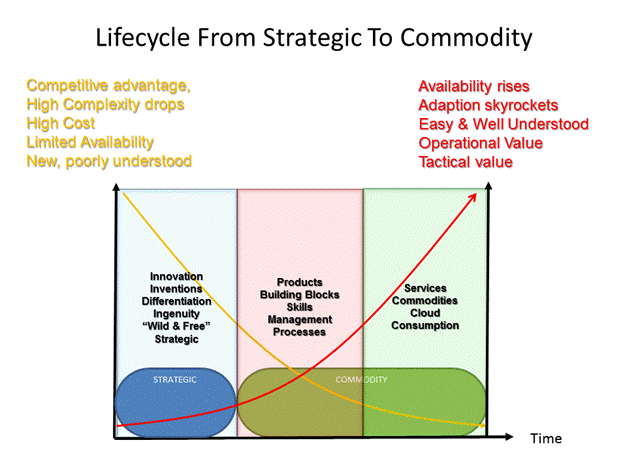
How do we get strategic IT?
That’s a hard question to answer. I can only give you my take on the subject. It’s far from complete but it addresses the way I look at it and how I try to do my part in achieving this. This is part 2 of a series on IT Strategies. Just some musings. You can find Part 1 here: https://blog.workinghardinit.work/2010/08/02/it-strategies-from-window-nt-3-51-to-the-cloud-era-part-1/
Merely leveling the playing field or value adding instrument?
Knowing what you have learned already, take a good look at the Total Cost of Ownership (TCO) and the Return on Investment (ROI) of the technology you own. You might wonder if any of those expensive IT systems are ever going to live up to all their potential. Can you easily pin point some real and substantial business benefits from your technology investments? We sincerely hope you can. Or do you have the “feeling” that most of that capital computing power is just sitting there idle and is hopelessly underused?
Use IT or lose IT!
Even in this day and age, it never ceases to amaze us how many routine and repetitive tasks are still done manually. IT can do two major things for your business. One is to improve physical operations by making them more efficient and the other is to reduce logical operations by automating as much of it as possible. If IT is not doing that, something is wrong. Why on earth are people reduced to mere (and rather slow and unreliable) biological processing units within the IT systems they work with? This not only wastes productivity but also leads to many avoidable errors that are not only time consuming to clean up but are often untraceable. The point is that you don’t want it to be like this and you need to fix it. This is not a question about wanting your technology to deliver value to your operations but needing it to do so. Not using your IT’s potential is literally squandering vast amounts of money. No business can afford to do that so you’ll either have to deal with that issue or risk losing funding for IT. Which means you’ll be even worse off. Any chance of ever recuperating the money you invested in technology has gone and funds to compete and get ahead of your competitors can only be dreamt of. This is not a good situation to be in and even harder to get out of.
Let’s face the fact that IT very often sucks at delivering value. That’s not technologies fault directly but it’s how we use it, or rather, abuse it. Business doesn’t know a thing about what IT can or can’t do and what’s the real cost of that. IT often is run by IT managers and CIO’s that are busier entrenching themselves in vast layers of expensive and often overly complex hardware and software. The IT industry itself is a willing accomplice. They really like to sell all that stuff and services as they love the color of money. They are partners in crime and hide that painful fact behind change management, methodology religion and an air of “we are keeping the sky from falling down”. But how do they explain it takes 14 days to restore a file server to service, that it costs 3 to 6 times more for enterprise IT to do than the market will bear? I’ll give you a hint, partially because the need to hire consultants to do their jobs. Why does it take over 4 years to consolidate to a new mail system in big government agencies? What happened Look, in corporate life a lot of what’s been doing done is bull shit and exists only to create career opportunities, to inflate ones importance and (they hope) ones wages. They built extremely expensive, large, complex systems that are hell to touch, let alone, change, improve or replace. People all follow their own time limited agenda’s and build up an extensive technology debt that will wreck a business sooner or later. But no one, not in business or in technology wants to acknowledge that. When you do bring it up and try to evangelize better ways you’re a bit of an annoying person rocking the boat. Hey, what we don’t need 10 consultants, a 20 person project team and 2 years to add a sub domain to Active Directory? What do you say? Our home build MIS that took 2 years and a couple of million € could have been bought for 3000,00- € with 80% of the features. That must be some real important report content that only our system can produce I bet! You think I’m joking? I hope you think that because you’re all doing it right and are not in an industry that will collapse by doing what I described above. Fast forward 10 to 15 years. What will “the cloud” have done to your little empire? Ok perhaps you’ll be retired by then, what if you’re 45 and a fake IT professional, developer or heaven forbid a fake consultant? Yeah you’ll call it age discrimination at the unemployment office, I’m sure, but what good will that do you really? But even then the true fakers will thrive. Never, ever forget that if the organization is large enough perception outperforms reality and, guess what fakers experts are at? Right! The most “reliable” consultants seem to work for organized crime these days (Consigliere). Make a mistake in that field of endeavor or don’t deliver and you find yourself standing on a piece of industrial plastic in the bosses office looking down the biggest and blackest hole you’ll ever see. And that shiny sliver of light at the end is most likely a Winchester Silvertip® Jacketed Hollow Point. They don’t buy crap services, only results.
Now What?
Now given all this, how the hell do we make IT a strategic asset? Well let’s first go and make sure we get a functional IT environment and then go for tactical, operational and strategic value. Just focusing on the strategy is not enough and even dangerous. The operational aspect is very important as well and you really do need both. To achieve strategic IT you really need to have an IT that’s functional. In the end you also need context, knowledge, skills, hard work and a “getting things done” attitude. Please do not think you can by this as a product or a service. You can only achieve an IT strategy by hard work and dedication. Trying to use recipes or methodologies without context is doomed to fail. It just doesn’t work. Unfortunately so many organizations really do that. Why? Because to many bad consultancy firms are milking those tools for the cash cows they have become. Look consultancy firms live by cheap personnel (to them, not to you) that get their jobs done by following guide lines, boilerplate documents and such. They couldn’t survive without them, the methodologies and processes are their life line. So when those don’t work they’ll sell you more of the same because that’s all they can handle and know. They don’t really care about your business. Essentially they are what are giving methodologies a bad name. They are used to let mediocre firms with mediocre or even incompetent personnel survive. Stay away from them. They have a hammer and they’ll use that tool everywhere for every job so basically they are frauds. This often continues way to long on because so much money is involved no one even dares to tell the truth anymore. Have you ever wondered why most over certified “BIG” corporations are hated and despised by their customers? They are over organized, to many weird processes. On paper all is well to perfect but in reality it doesn’t work anymore. This is probably the reason why we’re losing so many jobs in the West. We’re too expensive for the limited productivity we have and are burdened by the cost of dysfunctional methodologies. Are the other areas better? Nope they are cheaper, hungry for a better life and willing to make a real and prolonged effort.
Invest In Solutions & People
Basically what we’re saying is to stop buying technology and instead start investing in solutions. Solutions are built with technology. But there is more to it. Used correctly, technology can be a lot more than just a means to an end. The solutions built with technology must become an instrument that provides operational, tactical and strategic advantages to your organization. This means that IT will then realize its true potential.
So here is where your ICT staff (external or internal) can and must really differ from other commercial ICT providers or personnel. That piece of hardware and the operating system running on it is more to us than just a means to sell even more services, hardware and software. To us, it is the very basis of working solutions to real business issues. That’s the attitude we have towards addressing your problems. This requires knowledge, experience and dedication to finding the best approach for your organization.
This means that often you don’t have to buy yet more or new technology and software to solve problems. The best hidden secret in IT seems to be the value and opportunities that are available within most systems. It’s time for you to find them and be pleasantly surprised by what you what you already have but are not using. Use the money saved here to differentiate you in the market and be competitive. To achieve this you need knowledgeable people who care about the business.
Select your vendors and consultants with care. They should have one goal and that is to help you solve existing problems cost effectively and as a result deliver value to your company. They should not have the goal to sell only products or time to fix – perhaps even only perceived – problems. Think about it, you do not want to buy consulting hours, a dual CPU server or a body to fill an empty cubical. You want to buy a solution to an existing need. Of course we do work with vendors and other consultants in order to help you, but they have to agree and comply with our approach. If not, that’s a collaboration terminating event. It’s this attitude that helps us provide outstanding services. Yes we keep up to date on technology advances in our field of expertise, yes some of us are certified but we do not sell you acronyms and titles instead of skills. We are certified because we are experts, not vice versa. Most of all we are interested in learning about your business needs and matching them to satisfying solutions. Good consultants and IT Professionals will always seek the best way to help you. They will do this even when this means hiring others to do the job. If not, they are body shops who have only one goal, renting out people at daily rates. Walk away from these. They will never produce the results needed. Likewise, people just writing strategy documents, enterprise architecture designs and practice methodology religion that doesn’t improve or even relate to the realities in the field is nothing more than wasting money. They who do that are frauds. Why do I call this a “religion”? Because they only promise things later when you’re a good boy and when it never delivers you must have sinned against the methodologies? Oh please … enough already! Typical bullshit form people with no real field experience and knowledge, let alone the context to achieve something with methodologies.
A Vision on Realizing Solutions
Today anyone in the world with the right skills, attitude and motivation can provide services that result into high quality information technology solutions for any small, medium & large sized businesses around the globe. Fast internet connections in combination with secure remote administration tools have made this possible, especially when you realize that many technology implementations are being replaced by “good enough” services on the internet. Well, what good clients, employees and managers have in common is that they take their automation and computing needs seriously. However, they don’t always have the resources or know-how available to make the most of their investments in technology. By providing the necessary advice, assistance and implementation, technologists can add value to a company instead of delivering just another cost factor that merely levels the playing field. Solutions may range from single server systems over organization wide infrastructure roll outs to hybrid cloud implementations but the principle remains the same. We offer the knowledge and experience needed to make technology work for the business. A properly implemented IT solution can provide tactical, operational and strategic advantages in the market place. It makes you more competitive. To achieve these goals we rely on a number of key elements in any successful professional relationship.
Trust
All long term business relationships are based on mutual trust. Trust is not given away for free, it needs to be earned. You will need to establish a trust relationship between business and ICT in order for them to be your counselor and guide for current and future technology needs.
Integrity
Technology is a tool, a means to an end. Good IT offers to help your company use the tools it has or requires to their fullest potential. The business needs are important and IT should care about finding the right solution that the organization. An IT strategy must show commitment to work according to your needs and budget to find the right level of services and technology for your company. This needs to be done at a pace you can sustain. The goal is to add value to your business, not to extract money from it and waste time performing unnecessary tasks. On the opposite side, IT advisors must be honest and be able to walk away from organizations and managers who are not capable of being professional and have no real desire to improve. Only time and money can be wasted in such a situation. The money can be replaced. Our time cannot so it should never go to waste.
Reliability
All technology can and will fail at some point in time. Such events can result in lost data, lost time and lost revenue. Providing a business with a well-designed infrastructure however, will help you avoid such risks. This, in combination with excellent troubleshooting skills, facilitates recovering from such “disasters”. Keeping IT systems running smoothly requires a proactive approach consisting of maintenance and periodic auditing of the systems. The result of this is the reliability needed in order to prevent unscheduled down time. In the cloud era the ones responsible for all that change but the essence remains the same. Be advised however that everything can and will fail. Unbreakable does not exist. The differentiator is how we prevent it and how we deal with it when it occurs.
Attitude
You have a lot of choices when it comes to choosing someone to help you with your computing needs. Experience is one of the distinguishing factors, as is commitment, know-how and the ability to develop a vision about a company’s IT needs. This attitude provides guidance to organizations, so they can enjoy the benefits of well-designed computing systems without draining vast amounts of capital from their financial reserves.
Technology
Understanding technology is paramount to providing a great service. You cannot design and build something you do not understand. The correct mix of hands on experience, knowledge of complementing technologies and design skills, combined with continuous training is what enables IT Pro’s to optimize your technology investment.
Isn’t this going to very or prohibitively expensive?
This remark always provides for an opportunity to convince the person of the real value ICT can add. I have always made a genuine effort to position the IT solutions I design as qualitatively superior in both our approach and in the results we deliver. But that doesn’t mean they are overly expensive. Within our area of expertise, we will always seek to find the best and most cost effective solution that is viable to that particular business need. We will customize that solution to “tailor fit” the environment, but only if and when required. If IT is prohibitively expensive somebody is not doing their job right.
This, in my opinion, is a great way to provide an outstanding service and results; the value of which is reflected in the investment costs. How can you expect strategic IT and its implementation to be cheap? Good value for money, yes, but cheap, no. Now, some companies will never pay the rates and price needed to achieve this. Sometimes, in many ways, they are totally correct in not doing so. The most likely and best reason is that they do not need our services, i.e. it is just not worth it. For them IT is nothing more than a necessary and valuable commodity. The unfortunate reason is that our services can’t help them. Some simplified examples might help to clarify this. A lawyer who uses his laptop for writing reports and printing them out is not going to pay us 150 Euros per hour for setting up his free e-mail in Outlook, and he’s absolutely correct in not doing so. However, an organization that needs an effective, secure and rock solid virtualization solution will appreciate the benefits of good design and is willing to make that investment to achieve results. Until the day arrives the cloud does that better and more cost effective.
Costs for ICT and rates for personnel are not dictated by the complexity or the lack of complexity in an organization’s environment. Rates are established based on knowledge and the value IT brings to your business. An environment’s complexity only dictates how much time we will spend designing, implementing and/or supporting it, not how much time or solutions are worth. In the end you are engaging skills and knowledge, not time. Smart managers and IT architects simply refuse to compete with “low cost, low skill” operators who can only follow generic guidelines (if even that) and are stumped when “it doesn’t work”. But since you are reading this there is most likely a reason why you are looking beyond those players. You are interested in high quality strategic, tactical and operational ICT! So there you have it. It is the combination of skills, aptitudes, work ethics and intellectual capital that enables IT professionals to offer quality services that amount to added value and competitive advantage for your business. In the end, isn’t that what you want for your organization?
Think of any solution like a triangle. The three sides of the triangle have the following characteristics that can all be a quality by itself or combined together, depending on the circumstances.
- Cheap
- Fast
- Good
However be advised that the three sides combined together almost never materialize in real life. So you’ll have to pick two of them and, more or less, sacrifice the third. Which combination is needed depends on the issue at hand. Do not fool yourself into thinking that Information Technology is something that anyone can do by just reading a book, following some courses or owning a PC. It takes a tremendous amount of time, dedication and a sustained effort to become and stay competent and ahead in the world of IT, far beyond a 9 to 5 job. So realistically, if you expect this kind of expertise to be available at low ball rates or for free, perhaps it is time to take another look at the triangle and reevaluate your position on this. This is true in a mainframe, client server, web, Service Oriented Architecture and cloud world. The environment, technologies, tools and solutions change and we have to change with it.
Final Thoughts
It is important for both management and employees alike to realize that choosing a dynamic and scalable IT infrastructure solution in combination with a flexible and integrated development platform is very important. It provides one of the pillars for the successful implementation and support of the business strategy. Today this is no longer an opinion or a choice; it is a fact of doing business.
This means that these choices are as much a part of creating competitive advantage as any other strategic decision. The need to provide long term backward compatibility, support for current and new technologies, facilitate agile development and allow easy deployment and maintenance throughout its life cycle are paramount. All of this has to be done in an effective, efficient and affordable manner. These considerations are valid whether we are looking for a single line of business application or an entire infrastructure solution. Do realize solutions are fluid. There is no permanent solution, just the best solution at that moment for a certain period of time for that particular situation. That situation might be unique or it might be more common than muck. Much care must be taken not to build up an unsustainable technology debt and to keep working on reducing any non-managed debt present.
To end, never make the mistake of thinking that having a strategy is enough. You need the right people, the skills, the attitude and the guts where and when they are needed to execute your strategy. In essence it is never easy and it takes a lot of hard work. Plans and ideas that are not executed are worthless. Beware that acknowledging this must result in more than lip service to this vision. You must act upon it, translate it into plans, and provide leadership and guidance to achieve an IT strategy that will produce results. Money and tools are no substitute for solid skills and motivation. But those are subjects for another discussion. So for now, stop faking, study hard, work hard and build real good solid IT!
This is part 2 of a series on IT Strategies. Just some musings. You can find Part 1 here: https://blog.workinghardinit.work/2010/08/02/it-strategies-from-window-nt-3-51-to-the-cloud-era-part-1/

![clip_image002[5] clip_image002[5]](https://blog.workinghardinit.work/wp-content/uploads/2010/08/clip_image0025_thumb.gif)