Personal identity protection
In this blog post, we will use a FEITIAN BioPass FIDO2 Security key for personal identity protection. I already discussed using a FIDO2 security key for MFA in FEITIAN FIDO2 security keys – Working Hard In ITWorking Hard In IT. After that, we looked at configuring the biometric security key out of the box or after a reset in Configure a FEITIAN FIDO2 BioPass security key – Working Hard In ITWorking Hard In IT
Your online credentials do not only deserve but need adequate protection against abuse. That means protecting your credentials. Unfortunately, the reality is that the most used way of doing so, the user password combo, while ubiquitous, has been insufficient for a truckload of reasons for a long time. I will not address this here, but you can read about it all day long online.
Multifactor authentication comes to the rescue, and there are two prevalent and secure forms of this. First of all, we have the software-based solution in the form of an “authenticator” app that lives on a (hopefully) secured smartphone. The second is hardware-based security keys that protect your credentials in a secure, tamper-proof vault. These come in many interface forms, but USB-A or USB-C is very popular, and the most future-proof ones are FIDO2 security keys. I prefer FIDO2 keys with biometric capabilities. These allow us to go fully passwordless in use cases that support this.
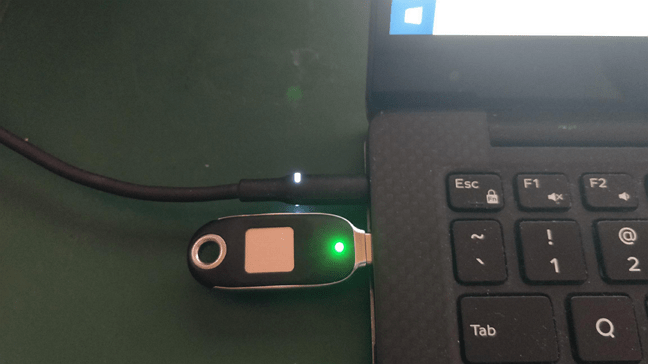
We set up a FEITIAN BioPass FIDO2 Security key for personal identity protection in our earlier blog post. Now we will use that security key to protect some of our online credentials for personal use.
FEITIAN BioPass FIDO2 Security key for personal identity protection
Microsoft personal account
Many of us have a Microsoft personal account. Think Outlook, OneDrive, Teams, etc. These are not just for O365 personal or business subscriptions but also work with Microsoft’s free offerings.
What I will do now is configure an account to leverage a security key. In this case, this is the FEITIAN BioPass FIDO2 K26 USB-C model I configured with my fingerprint in
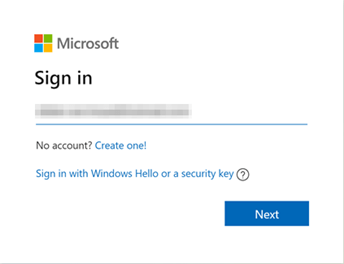
First of all, log in to your account via Microsoft account | Sign In or Create Your Account Today – Microsoft.
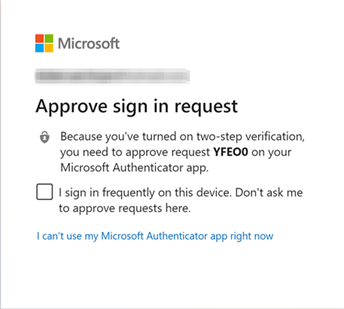
If you already have MFA set up, you might need to approve the challenge as I do below. In that case, your security key will become the second option for MFA.
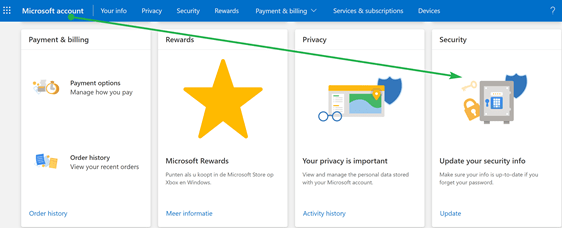
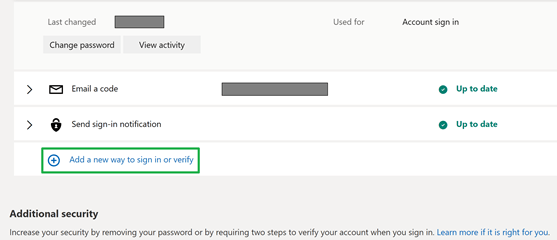
Once you log in, click on the security panel.
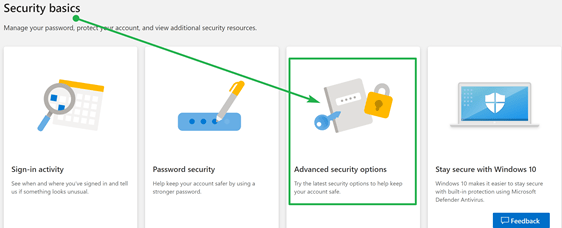
There you will find the” Advanced security options panel,” which you click.
Now you can “Add a new way to sign in,” which is what we want.
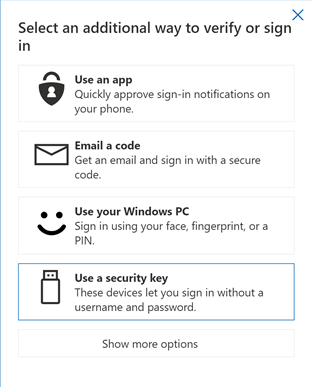
Select “Use a security key.”
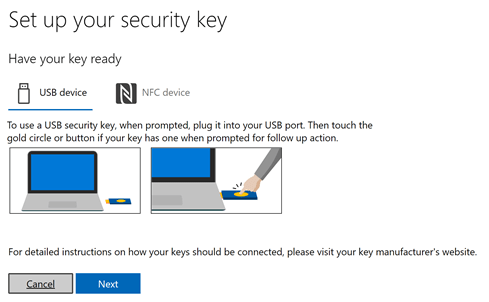
Next, you find the instructions on what you will need to do to onboard your security key, both in writing and via images.
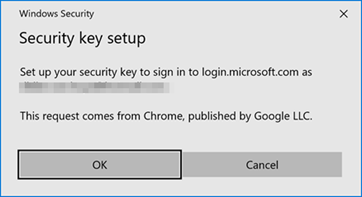
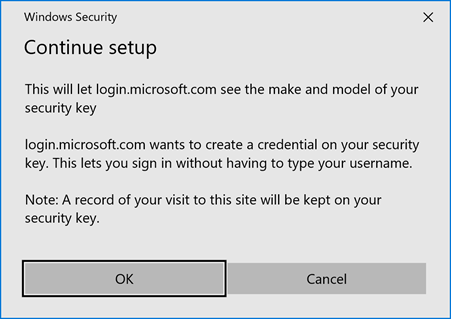
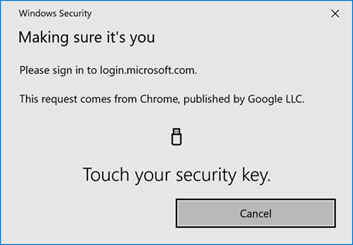
Windows Security notifies you that you are setting up your security key and tells you what application makes this request. In our example, it is the Chrome web browser.
Click “OK” and follow the instructions
Windows Security informs you that a credential will be stored on your security key so you can log in without having to type a username. Click “OK” to continue.
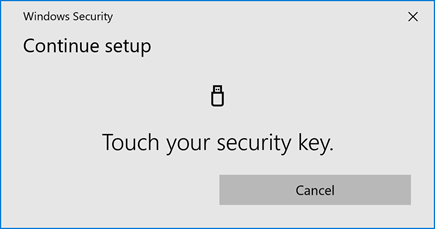
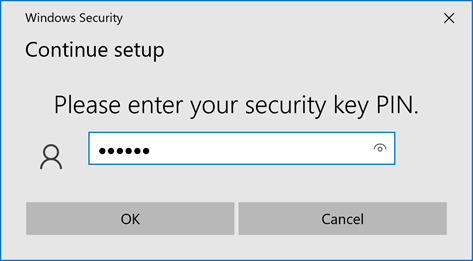
Touch the security key when requested. Remember we already stored your on the security key, but you need to provide your pin code to verify that this key belongs to you.
Enter your PIN-code and click “OK.”
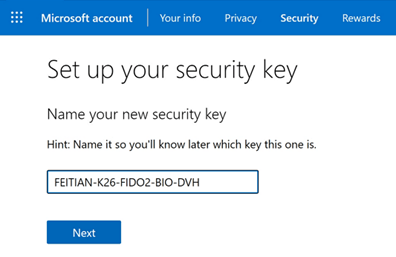
Touch your security key again, and this time it verifies a fingerprint of yours. When that is successful, you will see that you need to name your security name to identify which one it is quickly. Do so and click “Next.”
You have now successfully onboarded the security key and are ready to use it instead of a password.
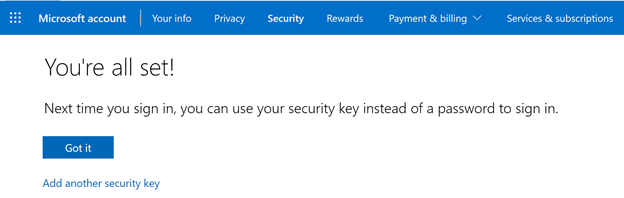
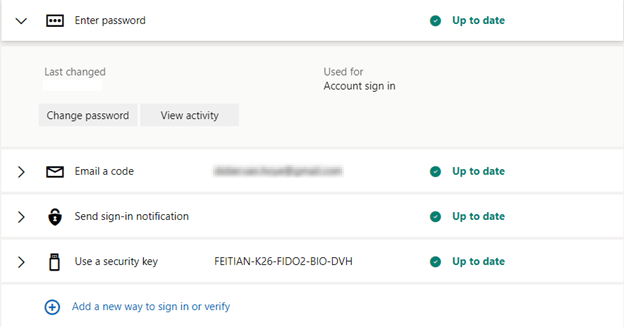
That is it. Tell me now, that wasn’t to be right? You can see the security key you added to your sign-in options.
Now that you have added the FEITIAN BioPass FIDO2 security key to your personal Microsoft account, you can now use it to log in to Outlook, OneDrive, and Teams. Of course, teams can be a bit picky when dealing with a security key and if your account belongs to multiple tenants as a guest user and you do not always use the tenant in which your account lives. But you can work through that.
Try it out!
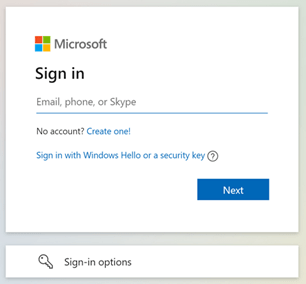
Open a private or incognito browser window, so you are not already authenticated. Then, navigate to Microsoft account | Sign In or Create Your Account Today – Microsoft. Click on “Sign In” to continue.
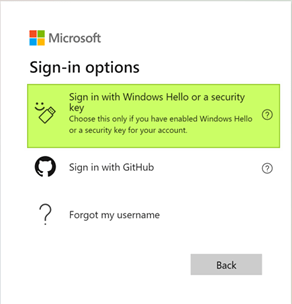
This time you select “Sign In with Windows Hello or a security key” or use the “Sign in options” button.
The security key is the option that you are after, so select that.
The form prompts you to touch your security key, which, as it is a FEITIAN BioPass FIDO2 device, will read your fingerprint and validate that.
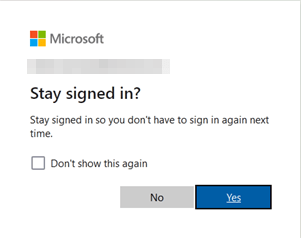
That will log you on. The following prompt asks if you want to stay signed in or not.
Realize that you no longer need to type in your username or password. Having the key is one factor. Knowing the PIN or presenting the fingerprint while touching the key provides for a secure second factor. Note that you might opt not to stay signed in for maximum security for the authentication always to be required.
Also, note that if you navigate to onedrive.com versus login.live.com, the experience is similar but different. When writing this article, in onedrive.com, you need to enter your account name before continuing and selecting another option for authentication than a password. With login.live.com, you get that option directly.
Finally, don’t forget that you can go genuinely passwordless and remove your password when you are ready to take that step.
Google account
Adding an MFA option to your google account is pretty straightforward. You have the option to add a security key next to push notifications to an authenticator app, a voice or an SMS message, or a Google prompt to a phone where you signed in with your Google account. Note that I gave the security key a sensible name for identification. See Use a security key for 2-Step Verification – Computer – Google Account Help for more information and guidance.
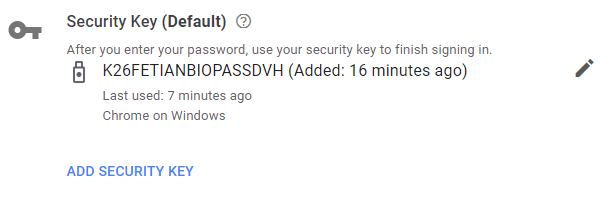
The above screenshot is of the FETIAN BioPass FIDO2 security key added to a Google account. Note that for now, Google does not let you go completely passwordless. The fingerprint on your security key is the second factor after entering your password. We’ll see how this evolves in the future.
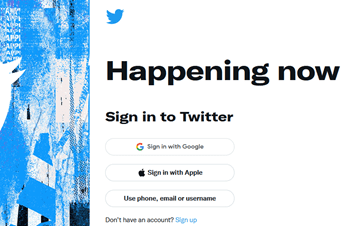
Recently Twitter also announced support for a security key in Stronger security for your Twitter account. Once you have done that, you will have a login process as described below.
First, navigate to twitter.com and select Sign in, where you opt for username, e-mail, or phone.
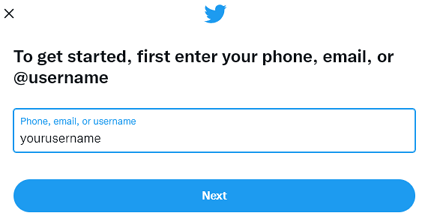
Fill out your username when requested. Click “Next” to continue.
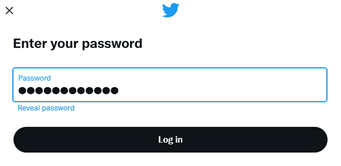
Enter your password en click “Log in” to carry on.
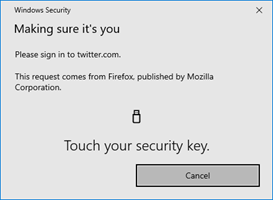
Now MFA kicks in, and you will need to touch your security key to respond to the MFA challenge. Note that you still have to enter your password here. You cannot (yet) go passwordless here.
The security key will read and verify (one of) your registered fingers prints and if that matches, allow your login. That’s it, and I am now reading my Twitter stream!
Call to action
First of all, start using MFA for your personal computing needs. Authenticator apps on smartphones are the usual first choice. Secondly, give FIDO 2 security keys a go either as a secondary or primary MFA device. While not all applications support a FIDO2 security key, many do, and I encourage anyone to try it out and see where it fits in. On that note, you can even use it for access to your Windows laptop or PC and even servers with the right (free) MFA provider and software. That means you have the best possible protection even when Windows Hello is unavailable to you due to a non-compatible camera on your client or because it does not work for your use case.
When and where supported, you are now ready to go passwordless, and you have at least two forms of MFA set up. Last but not least, you have your recovery keys and know the recovery process for your services when you lose access to a service. Well done!



Pingback: Your organization does not allow you to add your account to Microsoft Authenticator - Working Hard In ITWorking Hard In IT
Feitian is Chinese company & product. It might be a factor in selecting a hardware key to store one’s top credentials.
If that is a concern … what isn’t made of Chinese parts? Have them pen tested / audited and approved or discarded. And don’t only do this for Chinese (security) products, but any vendor from any country.