Introduction
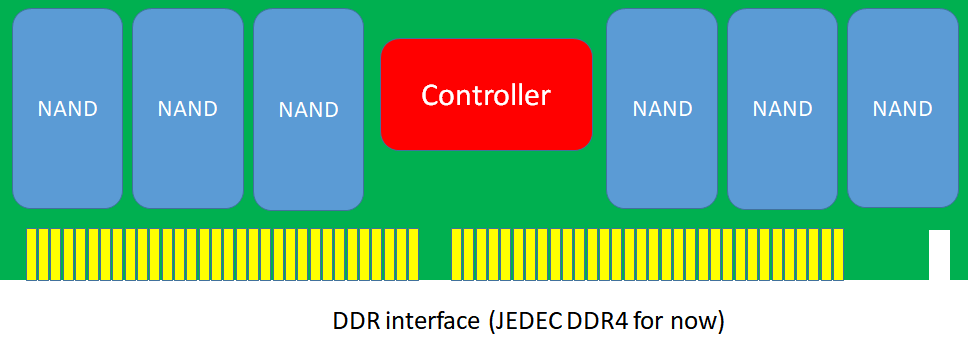
I made a rough video on how to configure Persistent Memory for Hyper-V. The server in this demo is a DELL R740. The type of persistent memory (PMEM) is NVDIMM-N. There were 6 modules in the system. In collaboration with my fellow MVPs Carsten Rachfahl and Anton Kolomyeytsev I hope to showcase storage class memory (SCM) as well (Intel Optane DC Persistent Memory, and later also NVDIMM-P). I can only hope that NRAM gets to market for real in 2020 so we can get memory class storage (MCS) out there. That would change the storage and memory world even more. If it can live up to its promise.
The video
In the video on how to configure Persistent Memory for Hyper-V, I walk you through the NVDIMM configuration in the BIOS first. Then we configure the PMEM regions on the host to get PMEM Disks.
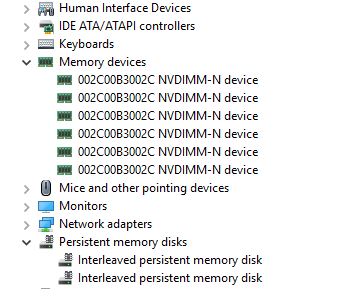
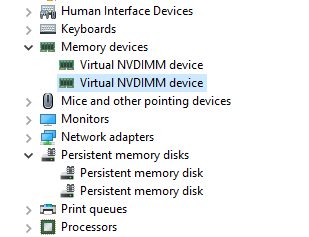
After initializing and formatting them we create the new .vhdpmem type of virtual disk on them. The virtual machine we want to present them to requires a new type of storage controller, a virtual machine PMEM controller, to be able to add the .vhdpmem disks. Once you have done that the PMEM disks will be visible inside the virtual machine.
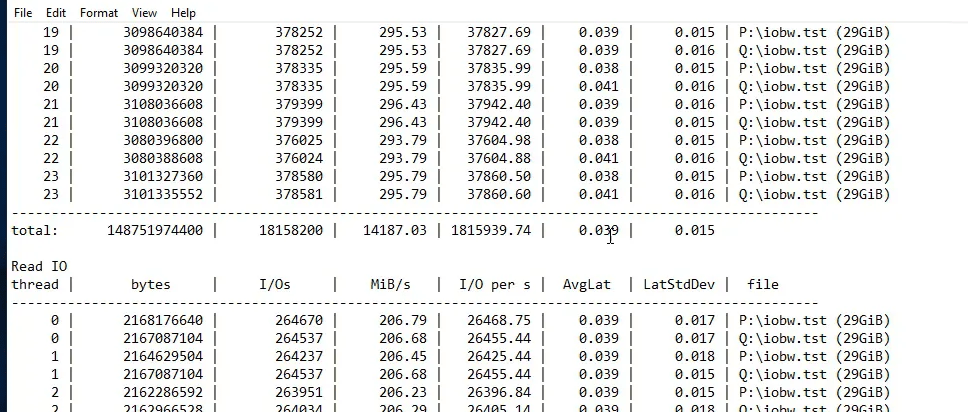
Inside the virtual machine, we initialize those PMEM disks and format them with NTFS. We put some large test files on them and run a diskspd test to show you how it performs. That’s it.
Enjoy the video on Vimeo here or below.
Powershell
Below you will find the PowerShell I used in the video. Adapt where needed for your setup and configuration.
PowerShell on the host
<# Didier Van Hoye Microsoft MVP Cloud & Datacenter Management Twitter: @WorkigHardInIT blog: https://blog.workinghardinit.work #> #Take a look at the unused PMEM regions Get-PmemUnusedRegion #We don't have PMEM disks yet Get-pmemdisk #We create PMEM disks from the unuses regions Get-PmemUnusedRegion | New-PmemDisk -AtomicityType None #Greate PMEM disk out of the unused regions #New-PmemDisk -RegionId 1 -AtomicityType None #List the PMEM disks Get-pmemdisk #Grab the physical disk that have Storage Class Memory (SCM) media or bus type. Get-PhysicalDisk | Where Mediatype -eq SCM | ft -AutoSize Get-Disk | Where BusType -eq SCM | ft -AutoSize #Initialize the pmem disks Get-Disk | Where BusType -eq SCM | Initialize-Disk –PartitionStyle GPT #Take a look at the initialized disks Get-Disk | Where BusType -eq SCM #Create partitions and format them New-Partition -DiskNumber 6 -UseMaximumSize -driveletter P | Format-Volume -FileSystem NTFS -NewFileSystemLabel PMEM01 -IsDAX $True New-Partition -DiskNumber 7 -UseMaximumSize -driveletter Q | Format-Volume -FileSystem NTFS -NewFileSystemLabel PMEM02 -IsDAX $True Get-Partition | fl * Get-Volume -driveletter P,Q | Get-Partition | ft Driveletter, IsDax #Show that the volumes are DAX fsutil fsinfo volumeinfo P: #On those PMEM disk with a DAX file system we create a VHDPMEM virtual disk New-VHD 'P:\Virtual Disks\DEMOVM-PMDisk02.vhdpmem' -Fixed -SizeBytes 31GB New-VHD 'Q:\Virtual Disks\DEMOVM-PMDisk02.vhdpmem' -Fixed -SizeBytes 31GB Get-VMPmemController PMEMVM (Get-VMPmemController PMEMVM).Drives #We add a virtual PMEM controller to our VM #make sure the VM is shut down. Add-VMPmemController PMEMVM #Check if it is there Get-VMPmemController PMEMVM #We add our VHDPMEM virtual disks to the VM Add-VMHardDiskDrive -VMName PMEMVM -ControllerType PMEM -ControllerNumber 0 -ControllerLocation 1 -Path 'P:\Virtual Disks\DEMOVM-PMDisk02.vhdpmem' Add-VMHardDiskDrive -VMName PMEMVM -ControllerType PMEM -ControllerNumber 0 -ControllerLocation 2 -Path 'Q:\Virtual Disks\DEMOVM-PMDisk02.vhdpmem' #Check if the disks are there Get-VMPmemController PMEMVM (Get-VMPmemController PMEMVM).Drives #That's it on the host, we now go in to the VM and initialize and format our PMEM disk there for use.
PowerShell in the virtual machineGet-Disk | where bustype -eq SCM | ft -AutoSize Get-Disk | Where BusType -eq SCM | Initialize-Disk –PartitionStyle GPT New-Partition -DiskNumber 1 -UseMaximumSize -driveletter P | Format-Volume -NewFileSystemLabel VDISKVMPMEM01 -FileSystem NTFS -AllocationUnitSize 65536 New-Partition -DiskNumber 2 -UseMaximumSize -driveletter Q | Format-Volume -NewFileSystemLabel VDISKVMPMEM02 -FileSystem NTFS -AllocationUnitSize 65536