Some days you walk into environments were legacy services that have been left running for 10 years as:
- They do what they need to do
- No one dares touch it
- Have been forgotten, yet they provide a much used service
Recently I had the honor of migrating IAS that was still running on Windows Server 2003 R2 x86, which was still there for reason 1. Fair enough but with W2K3 going it’s high time to replace it. The good news was it had already been virtualized (P2V) and is running on Hyper-V.
Since Windows 2008 the RADIUS service is provided by Network Policy Server (NPS) role. Note that they do not use SQL for logging.
Now in W2K3 there is no export/import functionality for the configuration in IAS. So are we stuck? Well no, a tool has been provided!
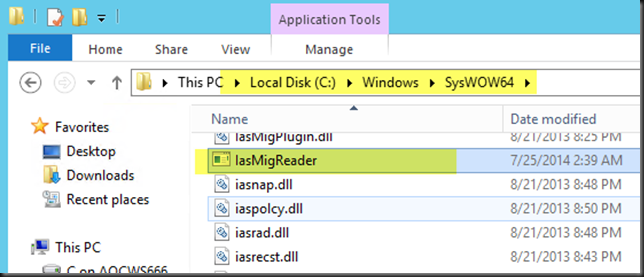
Install a brand new virtual machine with W2K12R2 and update it. Navigate to C:WindowsSysWOW64 folder and grab a copy of IasMigReader.exe.
Place IasMigReader.exe in the C:WindowsSystem32 path on the source W2K3 IAS server as that’s configured in the %path% environment variable and it will be available anywhere from the command prompt.
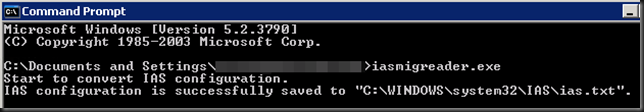
- Open a elevated command prompt
- Run IasMigReader.exe
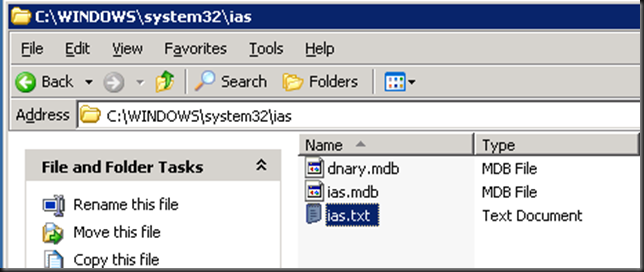
- Copy the resulting ias.txt file from the C:WindowsSystem32IASfolder. Please keep this file secure it contains password. TIP: As a side effect you can migrate your RADIUS even if no one remembers the shared secrets and you now have them again

Note: The good news is that in W2K12 (R2) the problem with IasMigReader.exe generating a bad parameter in ias.txt is fixed ((The EAP method is configured incorrectly during the migration process from a 32-bit or 64-bit version of Windows Server 2003 to Windows Server 2008 R2). So no need to mess around in there.
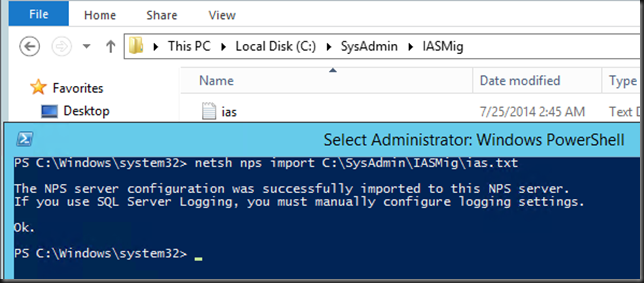
- Copy the ias.tx file to a folder on your target NPS server & run the following command from an elevated prompt:
netsh nps import <path>ias.txt
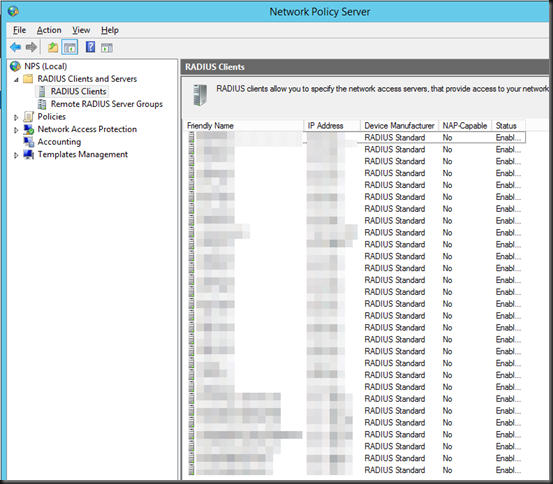
- Open the NPS MMC and check if this went well, normally you’ll have all your settings there.
- Important: Don’t forget to register the NPS Server in Active Directory, or things won’t work
 . See http://msdn.microsoft.com/en-us/library/cc754878.aspx:
. See http://msdn.microsoft.com/en-us/library/cc754878.aspx:
When Network Policy Server (NPS) is a member of an Active Directory® Domain Services (AD DS) domain, NPS performs authentication by comparing user credentials that it receives from network access servers with the credentials that are stored for the user account in AD DS. In addition, NPS authorizes connection requests by using network policy and by checking user account dial-in properties in AD DS.
For NPS to have permission to access user account credentials and dial-in properties in AD DS, the server running NPS must be registered in AD DS.
Membership in Domain Admins , or equivalent, is the minimum required to complete this procedure.
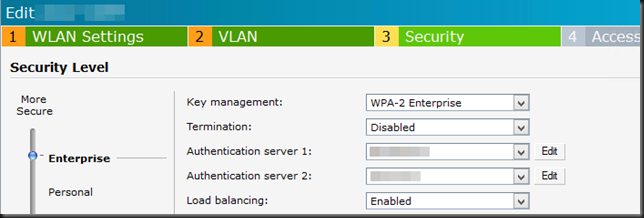
- All that’s left to do now is pointing the WAPs (or switches & other RADIUS Clients) to the new radius servers. On decent WAPs this is easy as either one of them acts as a controller or you have a dedicated controller device in place.
- TIP: Most decent WAPS & switches will allow for 2 Radius servers to be configured. So if you want you can repeat this to create a second NPS server with the option of load balancing. This provides redundancy & load balancing very easily. Only in larger environments multiple NPS proxies pointing to a number of NPS servers make sense.Here’s a DELL PowerConnect W-AP105 (Aruba) example of this.

I’m a little late to the server migration party, but this article helped simplify the process of moving to NPS. Thanks!
Great article which helped me enormously. However, it’s also worth noting that you may need to add certificates to your new server before the network policy will work. You’ll also need to ensure the server is registered with Active Directory (Action menu/Register server in Active Directory), although this option will be greyed out if it’s already been registered.
You’re welcome. Registering is mentioned with important in red 🙂
So it is! Apologies! 😉
To add new Radius Aut. server on Cisco WLC you need shared secrets. It´s not readable in ias.txt, correct? Will have to chance shared secrets, right?
Thanks in advance.
Last time I dumped a config into ias.txt it was as stated in the blog post. So if you’ve forgotten which one you used that how you can find it. Not sure if that’s changed since then.
NICE ARTICLE