Introduction
If you are anything like me, you want your labs and testing to mimic production as much as possible. Hence, when testing the Veeam Software Appliance and Veeam JeOS ISO installations in my Hyper-V lab, I want to use bonding for my LAN NICs and, potentially, for my dedicated backup network NICs. I say potentially, as that depends on the backup source and the available backup target networks, as well as the required configuration and the workloads they serve. Such design discussions have numerous permutations, which would lead us astray from the goal of this blog post.
Once we have decided we want bonding, the question at hand quickly becomes How does one get a bond to work in Linux VMs on Hyper-V? I will demonstrate how to do it for this specific use case. My primary concern was that the hardening of the ISO image might have blocked this from working, but it does not! Which is excellent news.
Yes, I know that bonding inside VMs is not the best approach, but we are doing this to emulate physical production configurations. In real-life production workloads, you should NOT even use virtual machines for hardened (immutable) repositories!
We need multiple NICs
First of all, we need a VM with multiple NICs. Two NICs for the LAN bond and then two or four NICs, depending on your network setup and goals. As stated above, we will not discuss this here.
I will direct you to a PowerShell script that allows you to easily deploy one or more scaffolding virtual machines on Hyper-V for testing the Veeam JeOS (Hardened Repository) ISO. Adapt the variables to your needs and run the script with elevated permissions. Locally, remotely, whatever suits you best.
You can set up the Hyper-V part of the NIC configuration for teaming via a script or in the GUI. I will use the GUI to showcase this, but will also provide the PowerShell commands in the script.
Note
You might remember my earlier guide on NIC bonding for Ubuntu guests in Hyper-V. There, I relied on full access to tooling on my Ubuntu servers. When working with the Veeam Hardened Repository ISO, things are more locked down. Thankfully, the installer provides a basic yet effective GUI. You can use it to configure NIC bonding during the installation process. Not only that, but we also have a basic menu-driven GUI after installation to configure and change the essentials. There should not be a need to SSH into the repository servers.
Bonding
This post guides you through setting up interface bonding during the initial installation phase using the built-in GUI, and I will show you where to configure or change it post-installation.
Installing the Veeam appliance & configuring bonding
They designed VeeamJeOS and other appliances with security in mind. That’s great for production, but it means you don’t get the same level of access to system internals as you do with a full-blown Ubuntu install. Specifically:
- You can’t easily view or manipulate MAC addresses.
- The repository is a stripped-down OS, so tools like ip, ifconfig, or even netplan might not be available.
- You’re working with a locked-down shell and a minimal set of packages.
- SSH access is available with one-time use passwords, and you need to enable it explicitly.
So how do we configure NIC bonding under these constraints? Let me walk you through this.
Step-by-Step: Bonding Interfaces in the Hardened ISO
1. Prepare Your Hyper-V Environment
Before booting the ISO, ensure your Hyper-V setup is ready. We will create a VM with an OS disk of at least 100 GB and add one or more larger data disks to emulate volumes backed by one or more RAID controllers. Don’t worry too much about the size, the disks are dynamically expanding ones and thin-provisioned. Naturally, you’ll need some vCPUs and vMemory. Additionally, create a Generation 2 VM and ensure that you set the secure boot template to “Microsoft EUFI Certificate Authority”. Last but not least, set the boot order to boot from the DVD drive first.
Next is the most important for this blog post: creating the vNICs.
- Create two LAN vNICs for your VM and two or more BACKUP vNICs.
- Enable MAC spoofing on the vNICs that you will bond inside the guest OS. It is crucial, as without it, the bond does not work correctly.
- You must check “Enable this network adapter to be part of a team in the guest OS.”
Lucky you, I have a scaffolding script to create such VMs for you, and you can find it here: https://github.com/WorkingHardInIT/CreateVeeamHardenedRepoScafoldingVMs
Change the variables to values that make sense in your lab and run it in an elevated PowerShell session.
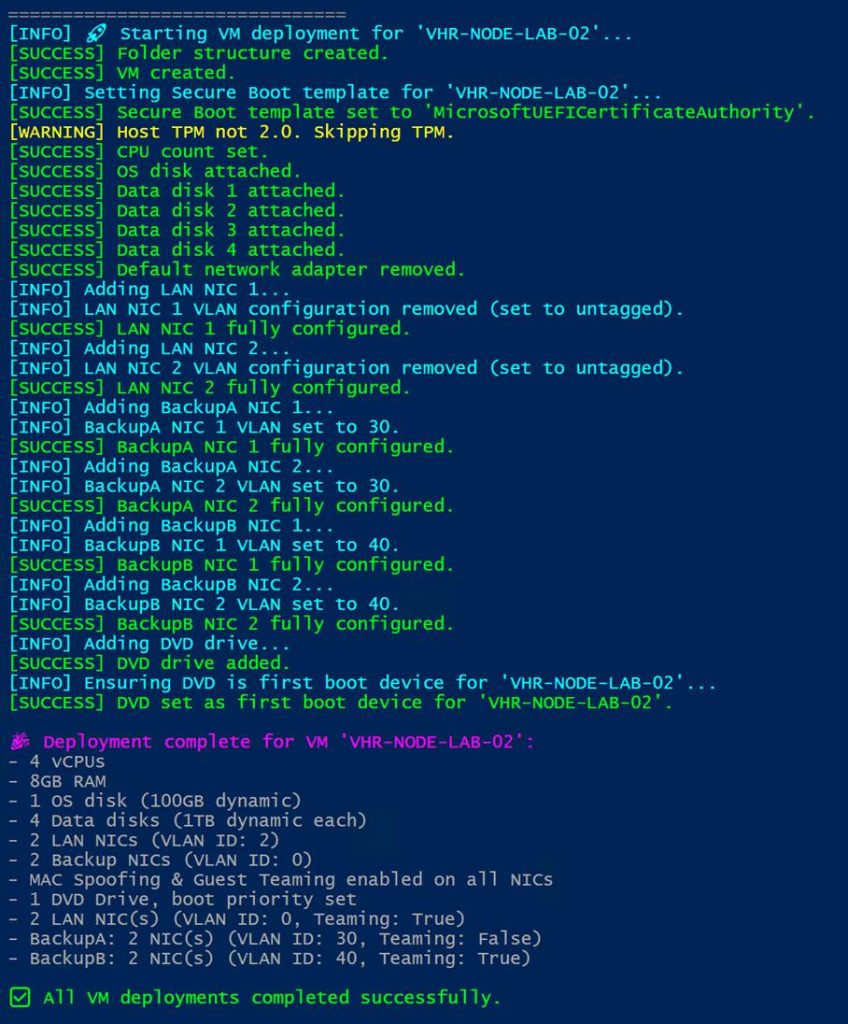
Enjoy. The only thing you need to do after running that script is mount the ISO in the DVD drive. You can play along with the VeeamHardenedRepository_2.0.0.8_20250117.iso or the VeeamJEOS_13.0.0.12109.BETA2.iso. In this article, I am using the VeeamHardenedRepository_2.0.0.8_20250117, as it is the current version suitable for production use. But if you follow the instructions below, you will be able to complete the process on both. For the V13 Beta 2, you need to contact Veeam as it requires an access code to download. You can watch a video of me installing VeeamSoftwareAppliance_13.0.0.12109.BETA2.iso with bonding here: https://vimeo.com/1108152527; the process is the same for the VeeamJEOS.
2. Boot the ISO and Access the Shell
Start the virtual machine.
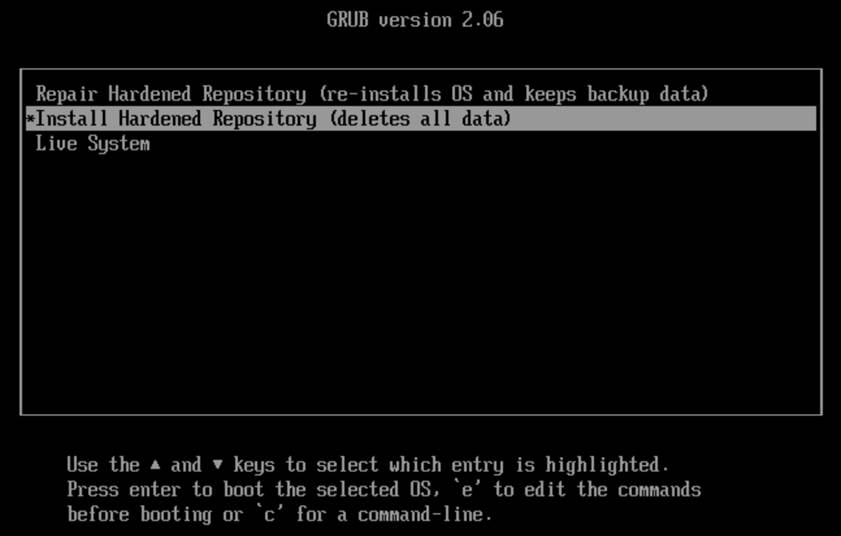
Once the virtual machine is running, you should see the installer splash screen. Select “Install Hardened Repository (deletes all data).” Hit ENTER to continue
Next, you will see the Installation Summary Screen. It is more limited than you might be used to with a standard Rocky Linux deployment.
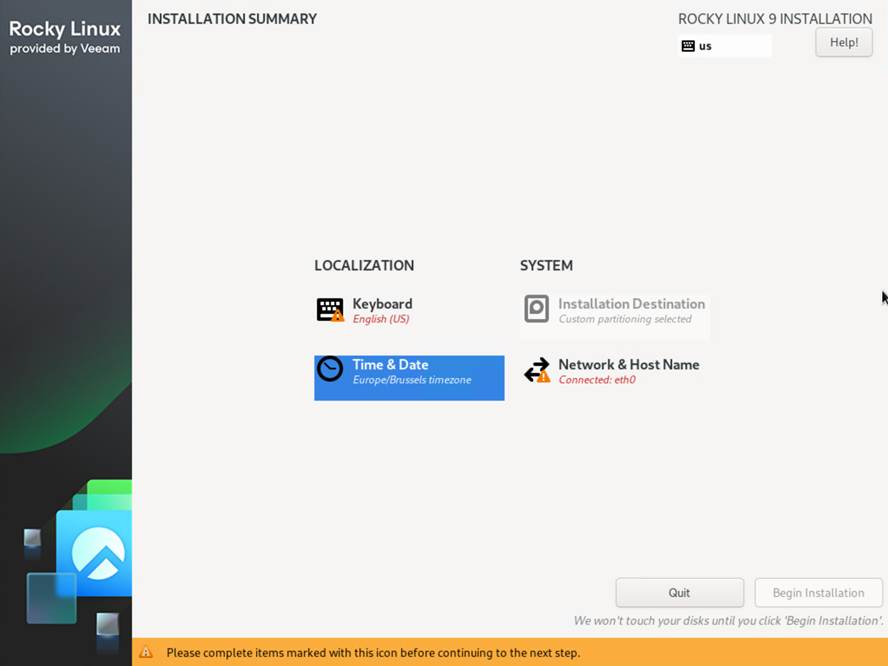
- Make sure the Keyboard is correct.
- Select your time zone (region and city)
- The installation (storage layout) is not configurable.
- The Network and hostname section is where we will do the most work!
3. Identify Your Network Interfaces
You should see all your NICs listed, and when you select one, you can also see the MAC address. That helps verify which Hyper-V vNIC this corresponds to. Usually, they are listed on both Hyper-V and in the OS (e.g., eth0, eth1, …) in the order in which the script created them.
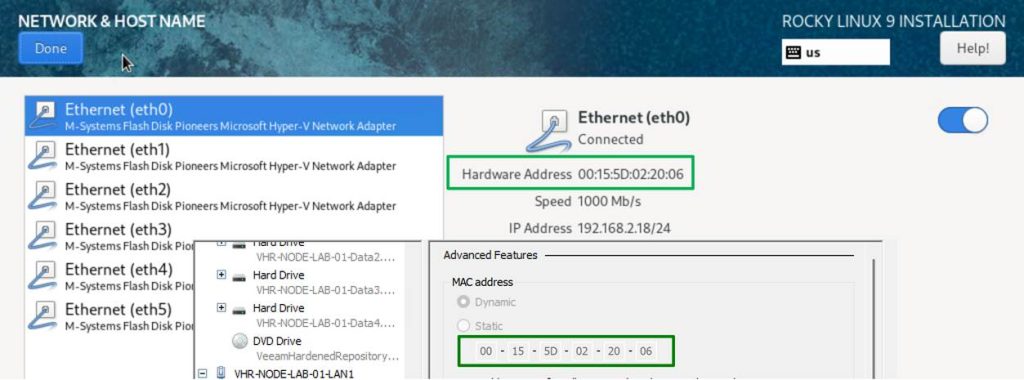
As you can see, one NIC got an IP address via DHCP, which is a good sign.
4. Create the Bond
Now, let’s set up bonding. Click the “+” button located to the left of the NIC listing.
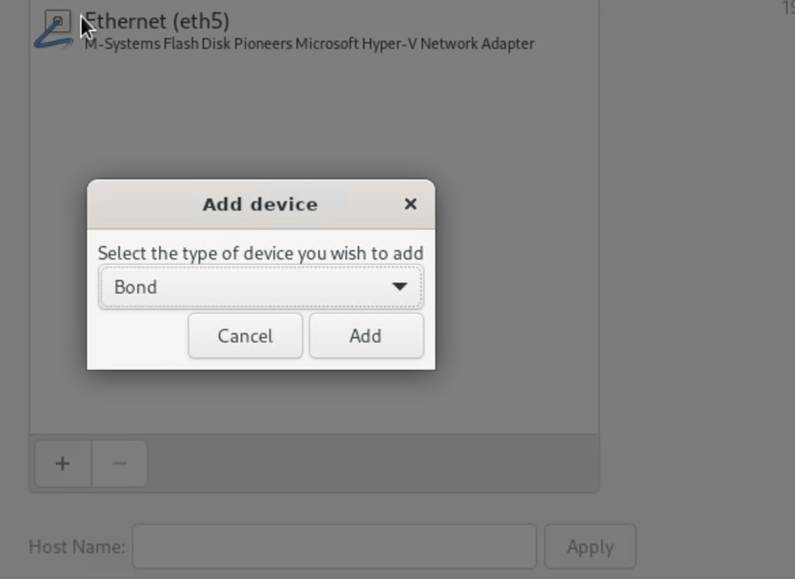
Ensure the type is “Bond” and click “Add”. Now configure the bond:
Please give it a distinguishable name, such as LANBOND
Give the interface a name: lanbond0
Add the interfaces. These are of type “Ethernet”
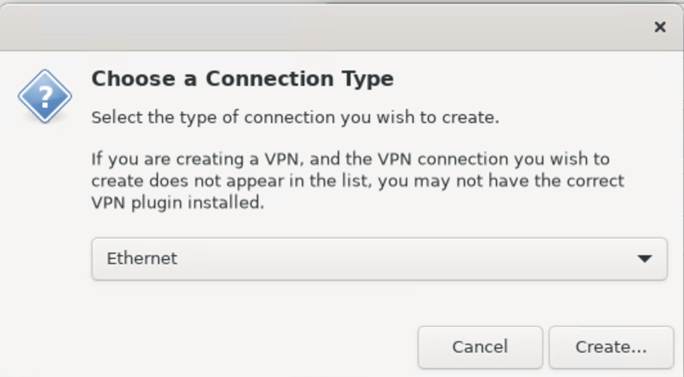
Click Create and add the devices. In this example, we will add both LAN NICs. Round-Robin is best here. LACP is not suitable for Hyper-V guest deployments. However, you can certainly use it in a physical production setup.
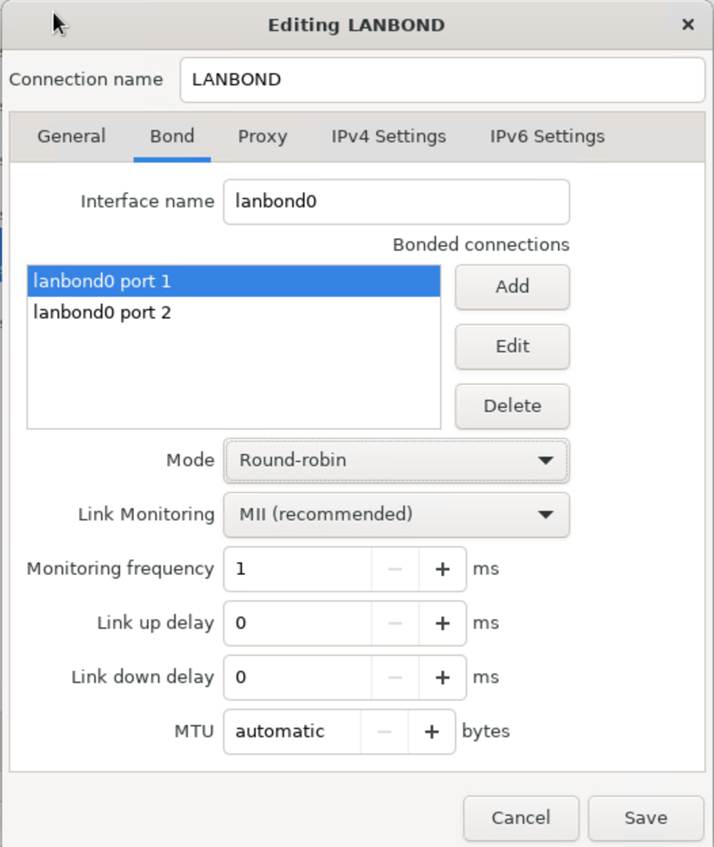
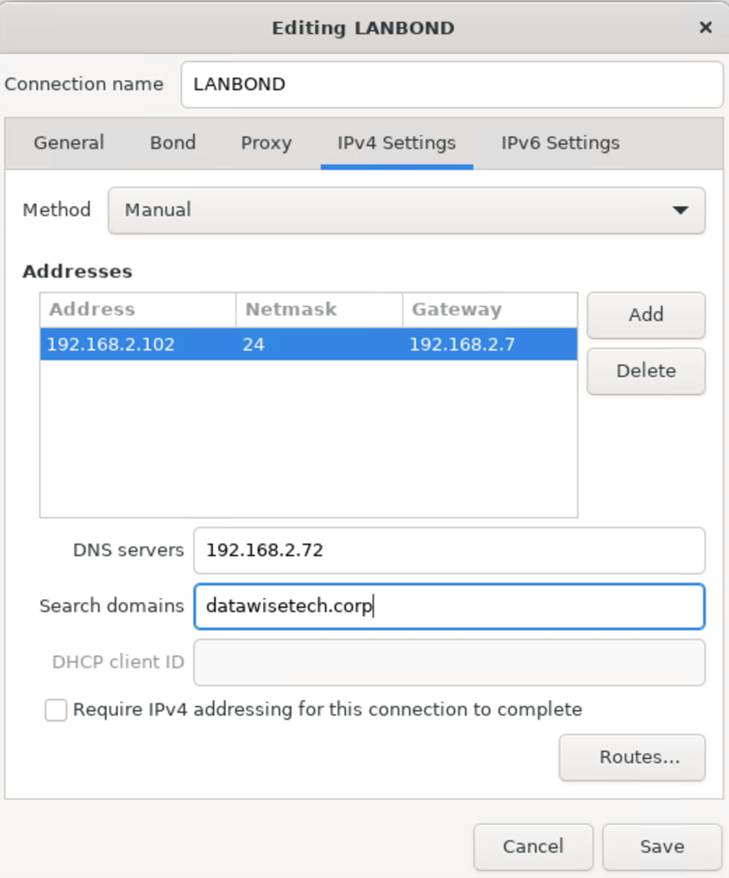
Save this and take a peek at the bond interface now. It has received a DHCP address. Good, now let’s configure our static IP settings. All this is pretty straightforward. Enter the correct data, including the NIC IP, subnet mask (in CIDR or Dotted Decimal Notation), gateway IP, and DNS servers.
5. Check your bond status and turn your bond off and on
Now pay attention to the bond. It will display the original IP address until you disconnect and reconnect. Use the toggle button for this. But there is more. Look at the MAC address. Yes, it has a spoofed MAC address of one of the member interfaces.
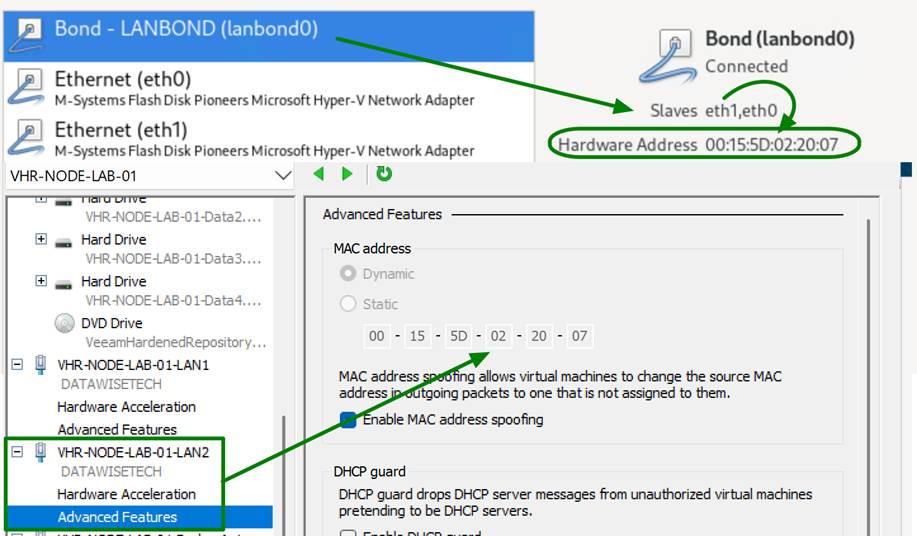
That is why you need MAC spoofing enabled on those bond member NICs in the Hyper-V setting of your virtual machine.
Finally, enter the host name and click Apply.

Click Done! You can already ping test the address; it should work.
Click “Begin Installation” in the lower-right corner of the splash screen. You will get a warning that this will wipe all disks. That is not a concern here. Click Yes. Let the installation process run. You can follow the progress.

Reboot the system when asked.
Log in using the following credentials:
- User: vhradmin
- Password: vhradmin
You must change the password to one that meets the minimal complexity requirements.
Accept the license terms.
You will have a menu to work with.
One of the things to do is configure the proxy setting, manage the network configuration, update your system, and start SSH with a single-use password.
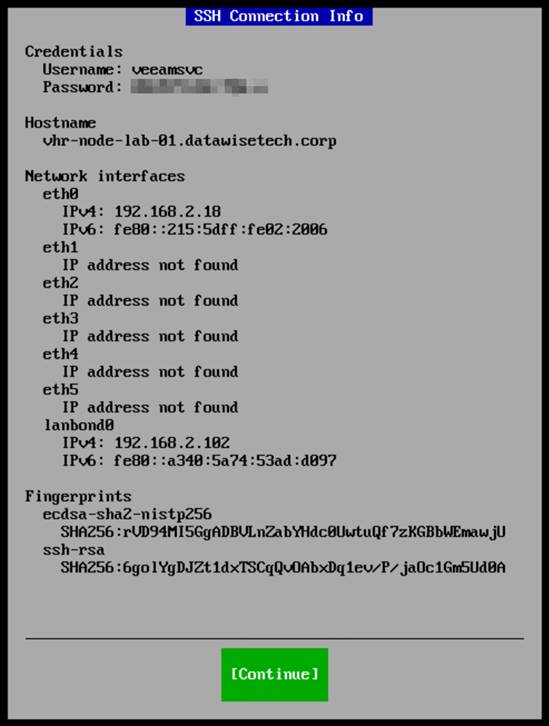
SSH gives you (controlled/protected) SSH access to take a peek under the hood or see if you can customize anything (lab only).
However, mainly, you need to temporarily enable SSH to add this repository to the Veeam fabric.
7. Troubleshooting tips
Look at your ping -t 192.168.2.101 replies. They should be returning an answer reliably! If not, here are some tips:
- First, ensure that you ping from only one test machine, as you can only send five pings per second. If you test from multiple machines and consoles, you will easily exceed this limit and experience drops.
- MAC Spoofing is non-negotiable. Without it, it won’t work
- Make sure “Enable the network adapter to be a part of a team in the guest operating system” is enabled.
- If you’re unsure which NIC is which, Hyper-V’s VM settings display the order in which you added them. But you can also use the MAC address to identify them via SSH if needed.
8. Bond failover testing
Once you have a reliable ping reply, do some further failover testing:
- Unplug one vNIC in Hyper-V and verify connectivity.
- Deactivate the members of the bond in Rocky Linux.
Note that you should not lose connectivity.
Conclusion
You are now ready to add that Veeam hardened repository to your Veeam Backup & Replication environment. Congrats.
Configuring bonding during installation with the GUI is surprisingly efficient. Suppose you forgot or want to change the configuration that is possible in the GUI provided by Veeam when you log on to the console. If you enable SSH, you can also use it to access the system; however, it is not necessary to configure bonding in this manner.
The Veeam Hardened Repository ISO is pretty slick! I like it a lot. I would like to see some flexibility in the backup storage configuration to allow for customization. I would also like to have MFA for console, SSH, and sudo actions, similar to what I have with Duo, which I use for my hardened repository builds. And guess what? Veeam is adding MFA to the JeOS ISO image with Veeam Backup & Replication 13. That, and mandatory Security Officer approval for privileged actions, under the ‘two pairs of eyes’ principle. Below is a sneak peek of that!
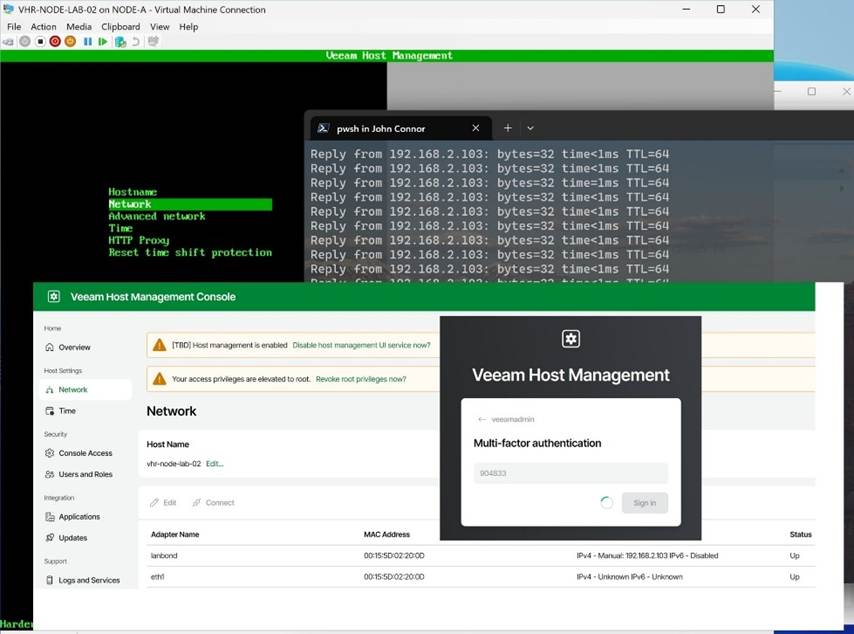
In lab environments running on Hyper-V, this blog post and my PowerShell script can help you get up and running quickly with redundant connectivity to reproduce production configurations. Please share your questions, experiences, or tweaks in the comments below.
