IIS and HTTP/3, QUIC, TLS 1.3 in Windows Server 2022
In this blog post, we will show you how to test IIS and HTTP/3, QUIC, TLS 1.3 in Windows Server 2022. As most of you know by now, Microsoft has released Windows Server 2022 on August 18th, 2021. There are a lot of new and interesting capabilities and features. Some of them are only available in Windows Server 2022 Azure edition. The good news is that in contrast to SMB over QUIC, QUIC for IIS is available in any version of Windows Server 2022.
This will not work out of the box, but I will demonstrate how I got it to work.
Getting TLS 1.3 to work
HTTP/3 uses QUIC for its transport, which is based on TLS 1.3 and Windows Server 2022 supports this. This is due to http.sys which leverages msquic. I have written about QUIC in SMB over QUIC Technology | StarWind Blog (starwindsoftware.com) and discussed SMB over QUIC in-depth in SMB over QUIC: How to use it – Part I | StarWind Blog (starwindsoftware.com) and SMB over QUIC: Testing Guide – Part II | StarWind Blog (starwindsoftware.com).
HTTP/3 avoids “head of line” (HOL) blocking at the transport layer even for multiple streams. This is an improvement over HTTP/2 that still suffered from HOL despite heaving multiple streams in a single connection versus multiple connections in HTTP/1.1. As HTTP/3 leverages TLS 1.3 it also benefits from the benefits it offers.
However, you need to opt-in for TLS 1.3 to work. We do that via a registry key.
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\HTTP\Parameters" /v EnableHttp3 /t REG_DWORD /d 1 /f
Without TLS 1.3 you cannot have QUIC and HTTP/3 used QUIC for its transport. You will need to restart http.sys or restart the server.
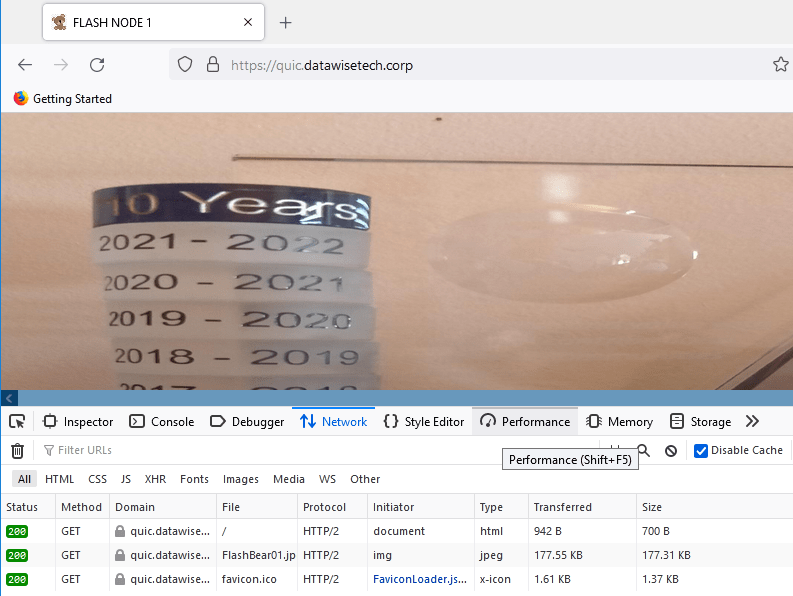
Below you see HTTP/2 traffic and it is leveraging TLS 1.3
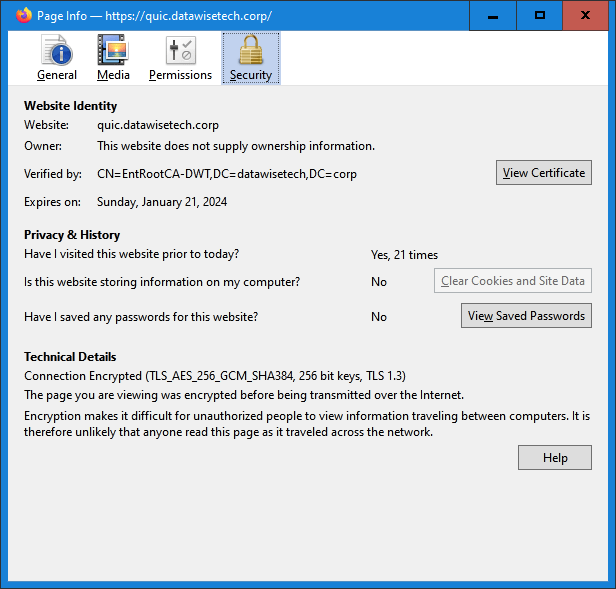
When you check the certificate in the browser you can see that TLS 1.3 is used.
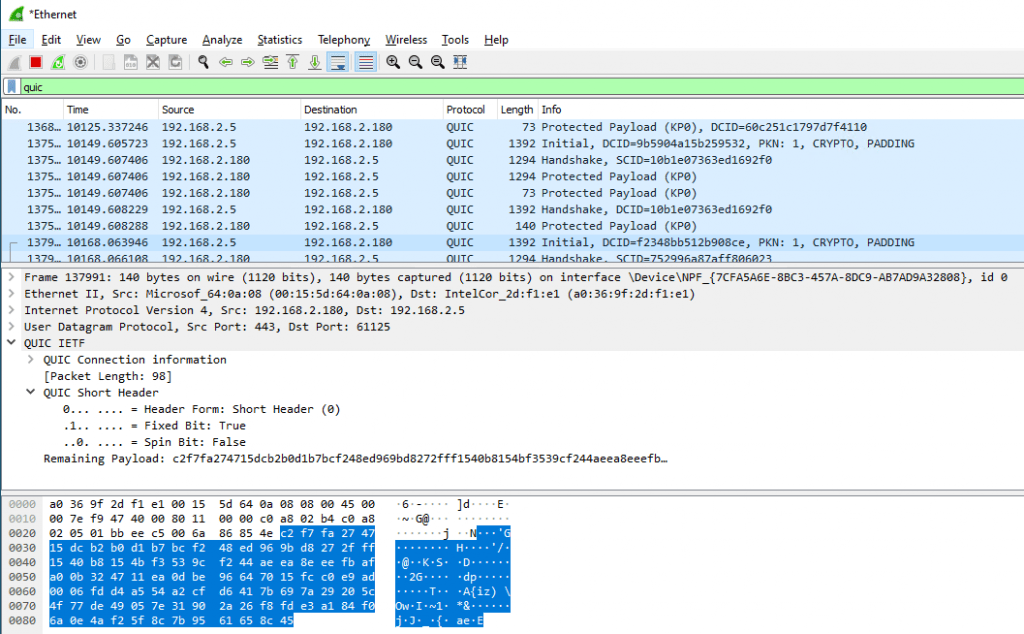
You can also see TLS 1.3 and TCP in WireShark.
Getting QUIC to work
Now we are not done yet, your while you now will see HTTP/2 traffic use TLS 1.3 you won’t see QUIC yet. For that, we need to add another registry key.
The web service or site will need to advertise it is available over HTTP/3. For this, we can use “Alt-Svc” headers in HTTP/2 responses or via HTTP/2 ALTSVC frames. Clients who connect over HTTP/2 can now learn the service’s HTTP/3 endpoint and, if successful, use HTTP/3.
This process happens by sending an HTTP/3 ALPN (“Application-layer Protocol Negotiation”) identifier along with the HTTP/2 responses. the HTTP3/ALPN advertises a specific version of HTTP/3 that the client can use for future requests.
The HTTP/2 ALTSVC frames can be sent via http.sys. This needs to be enabled via a registry key “EnableAltSvc”.
"HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\HTTP\Parameters" /v EnableAltSvc /t REG_DWORD /d 1 /f
Again, you will need to restart http.sys or restart the server.
Start testing HTTP/3
Your IIS server via the http.sys service is now capable of serving content over HTTP/3. To check whether it is working you can use WireShark on both the client and the server to verify the web traffic is using QUIC.
Below you can see QUIC traffic to my IIS server being captured.
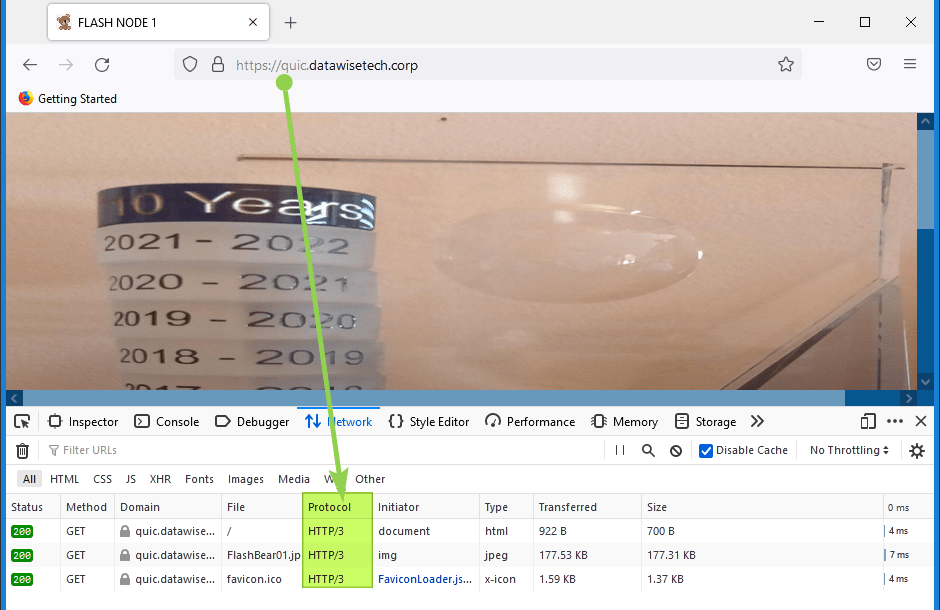
You can also check this via your browser’s dev tools. The way to do this differs a bit from browser to browser. Below you find a screenshot from Firefox, this has proven the most reliable browser when it comes to effectively negotiating QUIC. Hit F12, select “Network” and add the protocol column to the view. Watch out for HTTP/2 and HTTP/3.
It will help to hit refresh to make sure HTTP/3 is advertised to the client, which can then leverage it. Sometimes hitting refresh too much seems to break QUIC and then you will fall back to HTTP/2, all be it with TLS 1.3.
Any way that’s it for IIS and HTTP/3, QUIC, TLS 1.3 in Windows Server 2022 for now. I hope to come back to this later.


Thank you for your great article. I was missing 1 important step in the process to get it to work, opening the UDP 443 port on the firewalls. It was so obvious, that I somehow overlooked it. But it was staring me in the face all along. QUIC –> Quick UDP Internet Connections. It now works like a charm.
Happy to hear this helped you get it working. Thx for reading!
I followed the guide but my site still shows TLS 1.2, I don’t see TLS 1.3, why isn’t it working?
Quic seems to have some issues… try running a batch like so… your httperr log will FILL with errors, sadly no other troubleshooting info in the log. firewall not involved here, issue appears over localhost too (by using –resolve)
[code lang=text]
:start
curl https://domain.tld -k –http3
goto start
[/code]
Please dont go enabling this on production servers without first testing
Pingback: GeekSprech(EN) Podcast Episode 86 – DeepDive into HTTP/3, TLS 1.3, SMB, QUIC | GeekSprech